One of the most interesting exploit kits we track is also a bit of an elusive one, and as such does not receive the same scrutiny as its RIG and Fallout counterparts. Underminer was mentioned in our Fall 2018 round up, and at the time was using CVE-2018-8174 (Internet Explorer) and CVE-2018-4878 (Flash Player up to version 28.0.0.137).
In mid-December, we noticed some changes with Underminer that prompted us to take a deeper look. This happened around the same time frame as new zero-days and proof of concepts were available, which is typically an opportune moment for exploit kit authors to integrate.
Previous version and artifacts
The CVE-2018-4878 vulnerability is somewhat easy to spot within network traffic because it leaves some artifacts behind. Indeed, we use these in our lab and correlate them with other IOCs.
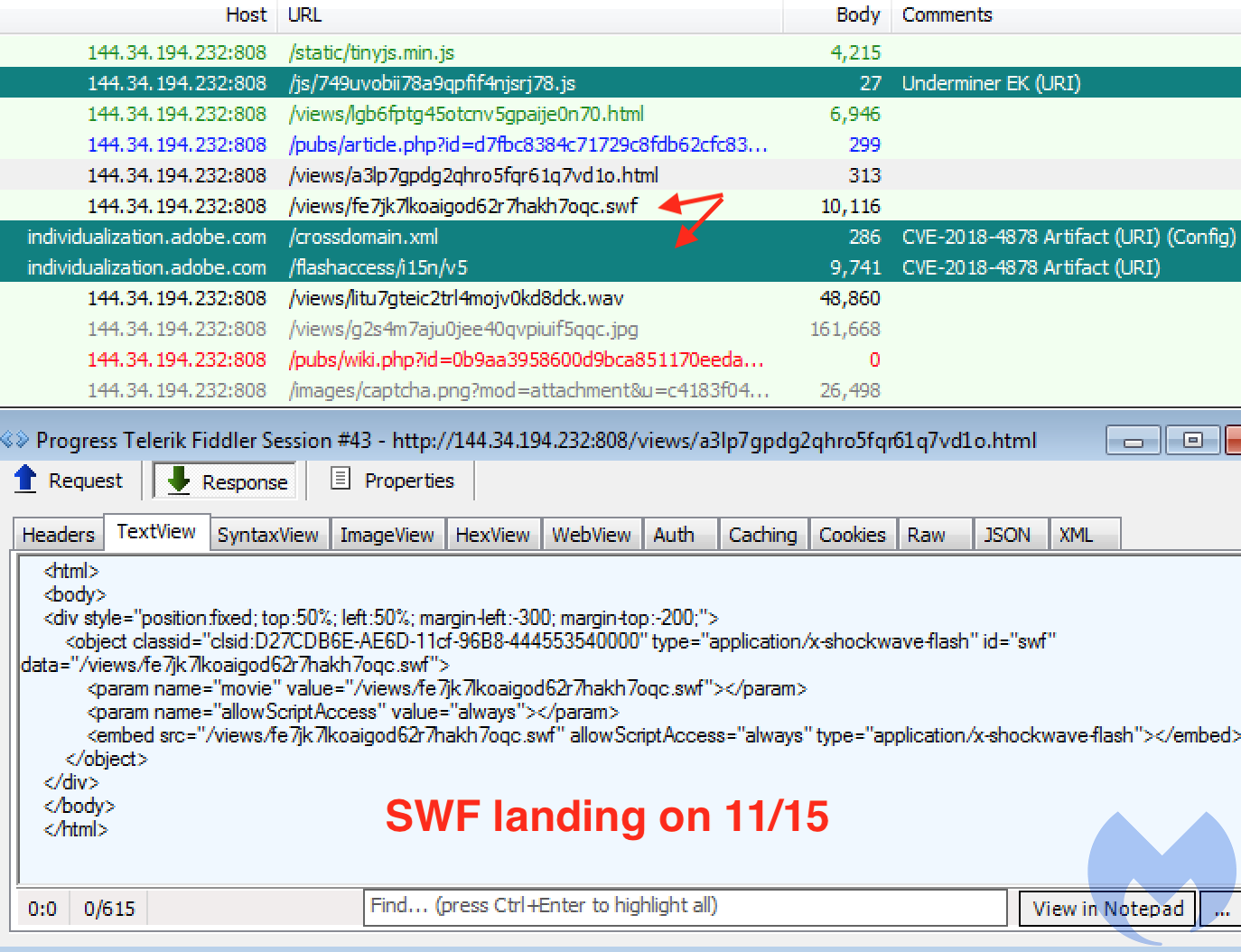
Traffic view of Underminer EK in November, showing CVE-20184878 artifacts
As documented in our previous blog post, Underminer uses client-server key exchange when it delivers its IE exploit, which encrypts the code but also prevents analysts from replaying it from a saved network capture. However, its SWF exploit up until now was deployed without such protections in place and could therefore be re-analyzed on its own.
New covert Flash exploit
The exploit appears to have changed as of mid-December. First, we did not see the Flash artifacts as we did before, which prompted us to test this exploit with a more recent version of Flash instead (31.0.0.153).
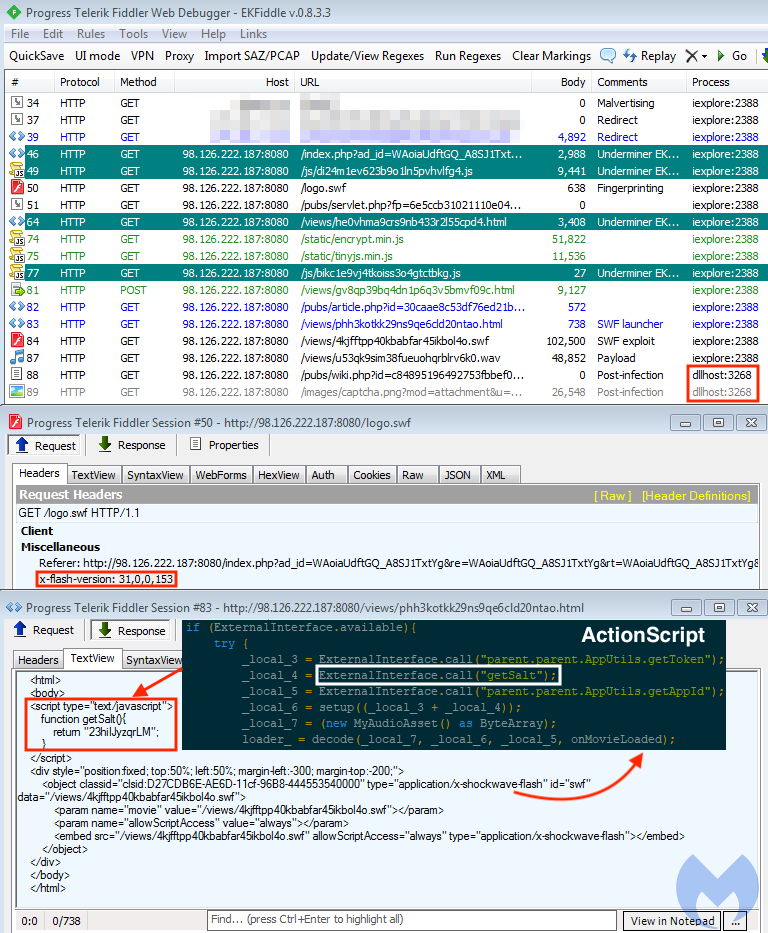
Traffic view of the latest Underminer EK using a different Flash exploit implementation
Second, we saw a new snippet of code within the SWF exploit landing page referencing a getSalt() function. This stoked our curiosity, and as we compared various traffic captures, we noticed that the function would always return different values.
Looking at the SWF exploit itself, we saw code that interacts with the launcher page’s JavaScript (ExternalInterface.call) and grabs that value in order to pass it to another function that decodes the exploit. When we attempted to replay the malicious SWF “artificially,” it would not fire properly.
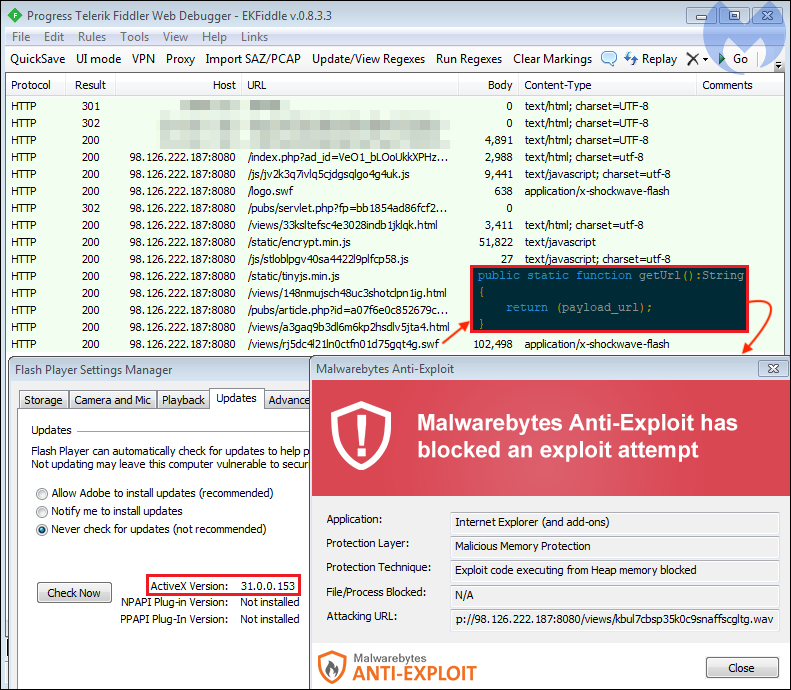
Malwarebytes Anti-Exploit triggering with Flash Player 31.0.0.153
Because the version of Flash we used was 31.0.0.153 (the latest Flash Player was not affected in our tests), we believe Underminer implemented the recent CVE-2018-15982.
The way the final payload is packaged and executed remains unique to Underminer. It’s what we call Hidden Bee. Hidden Bee is a custom payload that has specific modules and lacks the structure of the typical PE format. For this reason, it is more difficult to analyze and gives the attackers more flexibility than if they were using simple shellcode instead.
Malwarebytes users are already protected against this exploit kit, as we block both the Internet Explorer and Flash Player exploits.
Indicators of compromise (IOCs)
Underminer IP:
98.126.222[.]187
Flash exploit
d75710ebc8516e73e3a8dd7d1ad1ebc3221b7a141659c7e84b9f5f97dd7ec09e
Custom payload
5574f4b0b507130db06072930016ed5d2ef79aaa1262faddfdb88891c1599672










