Microsoft is getting criticized for the way in which it handled a serious security incident that allowed a suspected Chinese espionage group to access user email from approximately 25 organizations, including government agencies and related consumer accounts in the public cloud. The attacks were targeted and lasted for about a month before they were first discovered.
The investigation started on Jun 16, 2023, when Microsoft was notified by a customer about an anomalous Exchange Online data access. Investigation learned that the customer’s Exchange Online data was accessed using Outlook Web Access (OWA).
Microsoft analysis attributed the activity to a group called Storm-0558 based on established prior tactics, techniques, and procedures (TTPs). Attribution is based on Microsoft Threat Intelligence assessment that Storm-0558 is a China-based threat actor with activities and methods consistent with espionage objectives.
At first Microsoft assumed that the spies were using legitimate Azure Active Directory (Azure AD) tokens stolen by malware. But further analysis showed that Storm-0558 was forging Azure AD tokens using an acquired Microsoft account (MSA) consumer signing key to access OWA and Outlook.com.
This was only possible because of a validation error in Microsoft code. MSA (consumer) keys and Azure AD (enterprise) keys are issued and managed from separate systems and should only be valid for their respective systems. Microsoft says it still doesn’t know how Storm-0558 stole the inactive MSA signing key.
An authentication token allows internet users to access applications, services, websites, and application programming interfaces (APIs) without having to enter their login credentials each time they visit. Instead, the user logs in once, and a unique token is generated and shared with connected applications or websites to verify their identity.
These tokens are validated with a signing key, so with access to such a key an attacker is able to create valid tokens to access the associated services. Storm-0558 was able to obtain new access tokens by presenting one previously issued from GetAccessTokenForResource Application Programming Interface (API) due to a design flaw. This flaw in this API has since been fixed.
When asked, China denied it was involved and basically said people in glass houses shouldn’t throw stones.
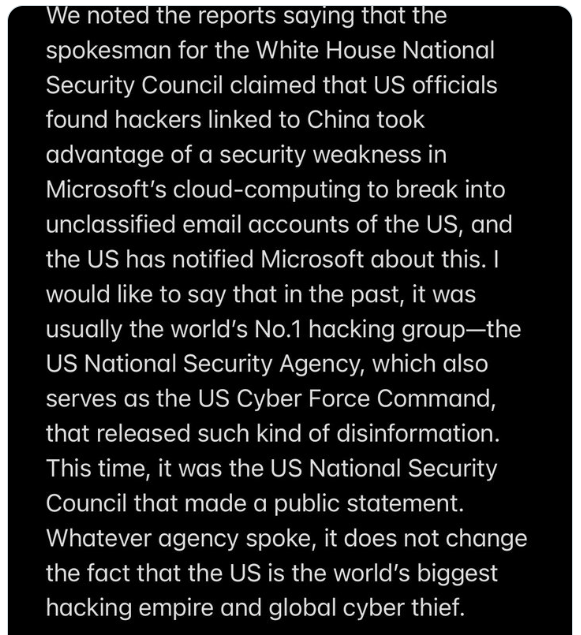
“We noted the reports saying that the spokesman for the White House National Security Council claimed that US officials found hackers linked to China took advantage of a security weakness in Microsoft’s cloud-computing to break into unclassified email accounts of the US, and the US has notified Microsoft about this. I would like to say that in the past, it was usually the world’s No.1 hacking group–the US National Security Agency, which also serves as the US Cyber Force Command, that released such kind of disinformation. This time it was the US National Security Council that made a public statement. Whatever agency spoke, it does not change the fact that the US is the world’s biggest hacking empire and global cyber thief.”
What has been done
Microsoft says it has completed mitigation of this attack for all customers and has not found any evidence of further access. The impacted customers have been contacted so no additional customer action is needed to prevent hackers from using the same tactics to access their Exchange or Outlook accounts.
On June 26, OWA stopped accepting tokens issued from GetAccessTokensForResource for renewal, which stopped Storm-0556 ‘s ability to use tokens issued from the Azure program.
On June 27, Microsoft blocked the usage of tokens signed with the acquired MSA key in OWA, blocking the usage of tokens signed with the key that had been acquired.
On June 29, Microsoft completed replacement of the key to prevent the threat actor from using it to forge new tokens.
Microsoft blocked the use of the stolen private signing key for all impacted customers on July 3, 2023 and says it has “substantially hardened key issuance systems since the acquired MSA key was initially issued.”
Malwarebytes EDR and MDR removes all remnants of ransomware and prevents you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.











