Results for 'botnet'
Phishing 101: Part 2
July 3, 2012 - “Over the years, phishing attacks have changed, as with most things, and have been segmented into different groups of variants.” –Me...
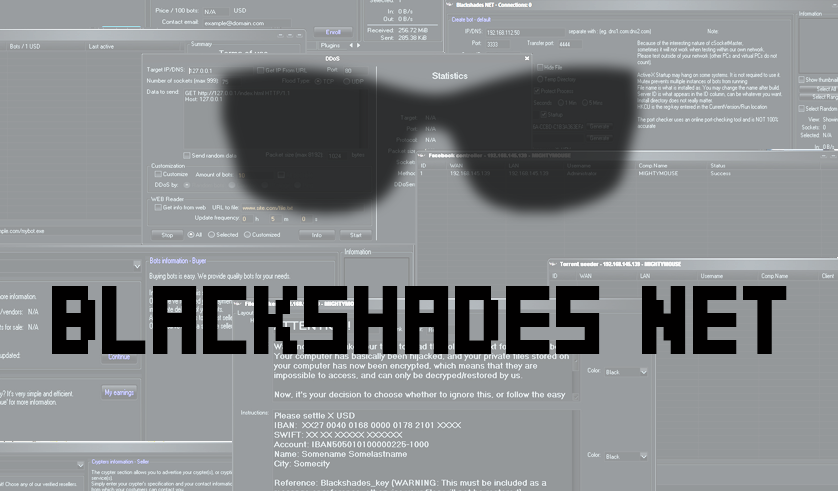
You Dirty RAT! Part 2 – BlackShades NET
June 15, 2012 - Last week we talked about the Remote Administration Trojan DarkComet and all the wonderful and scary things it can do. In...
You dirty RAT! Part 1: DarkComet
June 9, 2012 - Last week, I talked a little about the Flame Trojan and how much the average user would need to worry about...
RATs of Unusual Sizes
June 1, 2012 - The flame malware has been referred to by some as “The most sophisticated malware to date” and while it is quite...
Stopping malware distribution at the source
May 9, 2012 - At Malwarebytes we are a bit obsessed with protecting our users, which causes us to approach our jobs from all sorts...
Anonymizing VM Traffic (Introduction)
April 24, 2012 - WARNING: The information included in this tutorial could be used for malicious purposes in the wrong hands, please expect to be...