Results for 'safari'
A Week in Security (Oct 18 – Oct 24)
October 26, 2015 - Last week, we touched on a fake Java download, an Apple invoice phish, current tactics used by chip-and-PIN fraudsters, an upcoming...
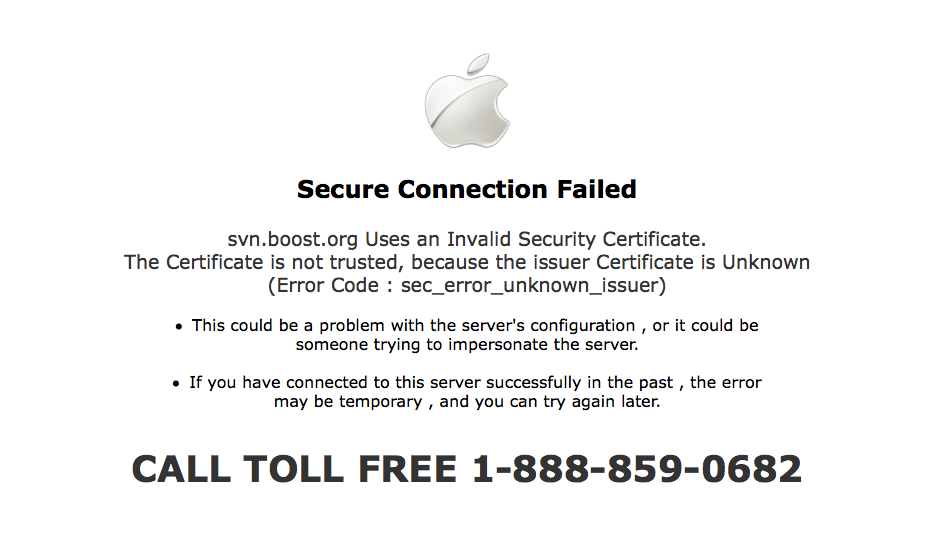
Tech Support Scammers Impersonate Apple Technicians
October 20, 2015 - Remote assistance is becoming more and more popular to troubleshoot computer issues without the hassle of bringing the problematic machine to...
XcodeGhost malware infiltrates App Store
September 21, 2015 - Late last week, Claud Xiao, a researcher at Palo Alto Networks, announced the discovery of new malware that he calls XcodeGhost....
A Week in Security (Aug 30 – Sep 05)
September 7, 2015 - Last week, we talked about a fake Android rooting tool, a supposedly unlimited offer of games that eventually ended in frustration,...
Genieo installer tricks keychain
August 31, 2015 - Earlier this month, an adware installer was found to be taking advantage of the DYLD_PRINT_TO_FILE vulnerability in OS X. Now Malwarebytes...
This PUP Alerts You of a Zombie Invasion
August 28, 2015 - Author’s Note: We at Malwarebytes continue to do our part in educating our product users and constant blog readers about day-to-day...
A Week in Security (Jul 26 – Aug 01)
August 3, 2015 - Last week, Malwarebytes announced that our line of security products now support Windows 10, Microsoft’s latest operating system to date. If...
Defeating The Fake iOS Crash Reports
July 31, 2015 - There have been a lot of reports lately about fake iOS crash reports that completely hijack your iPhone or iPad. Indeed, online...
Unusual Exploit Kit Targets Chinese Users (Part 2)
June 12, 2015 - Recently, our researchers identified a strange exploit kit targeting Chinese domains. In that writeup, we talked about how the exploit kit...
The Logjam Attack: What You Need to Know
May 20, 2015 - A group of security researchers and computer scientists have recently uncovered a vulnerability in how a Diffie-Hellman key exchange is deployed...