Let’s talk Ryuk ransomware
Ryuk is the name of a ransomware family, first discovered in the wild in August 2018. In the good old days, we knew Ryuk only as a fictional character in a popular Japanese comic book and cartoon series, but now we know it as one of the nastiest ransomware families to ever plague systems worldwide.
What is Ryuk ransomware?
Let’s start with defining ransomware in general. Ransomware is a category of malware that locks your files or systems and holds them hostage for ransom. Ryuk is a type of ransomware used in targeted attacks, where the threat actors make sure that essential files are encrypted so they can ask for large ransom amounts. A typical Ryuk ransom demand can amount to a few hundred thousand dollars. Malwarebytes detects it as Ransom.Ryuk. For a more in-depth technical look at this threat, see our Ryuk ransomware threat spotlight.
How does Ryuk work?
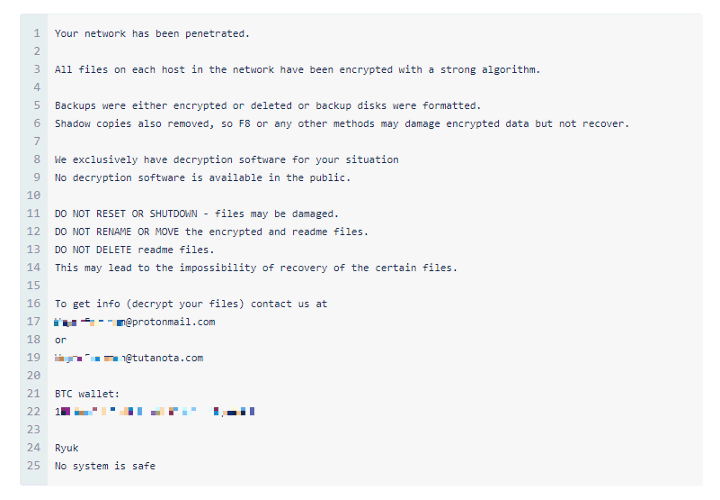
Ryuk is one of the first ransomware families to include the ability to identify and encrypt network drives and resources, as well as delete shadow copies on the endpoint. This means the attackers can then disable Windows System Restore for users, making it impossible to recover from an attack without external backups or rollback technology.
Who created Ryuk?
Malware attribution is always hard. However, researchers at Deloitte Argentina, Gabriela Nicolao and Luciano Martins, attributed Ryuk ransomware to CryptoTech, a little-known cybercriminal group that was observed touting Hermes 2.1 in an underground forum back in August 2017. Hermes 2.1, according to the researchers, is another name for Ryuk ransomware.
Ryuk ransomware news
- 2021:
- 2020:
- 2019:
Who are Ryuk’s targets?
Ryuk’s targets tend to be high-profile organizations where the attackers know they are likely to get paid their steep ransom demands. Victims include EMCOR, UHS hospitals, and several newspapers. In targeting these organizations, Ryuk was estimated to have generated a revenue of $61 million for its operators between February 2018 and October 2019.
How is Ryuk delivered?
As with many malware attacks, the delivery method is spam emails (malspam). These emails are often sent from a spoofed address, so the sender name does not raise suspicion.
A typical Ryuk attack begins when a user opens a weaponized Microsoft Office document attached to a phishing email. Opening the document causes a malicious macro to execute a PowerShell command that attempts to download the banking Trojan Emotet. This Trojan has the ability to download additional malware onto an infected machine that retrieves and executes Trickbot, of which the main payload is spyware. This collects admin credentials, allowing attackers to move laterally to critical assets connected to the network. The attack chain concludes when the attackers execute Ryuk on each of these assets.
So, once your network has been breached, the attackers decide whether they think it’s worth the effort to further explore and infiltrate the network. If they have enough leverage to demand a large sum, then they will deploy the Ryuk ransomware.
How can I protect myself against Ryuk?
The first step in protecting against any ransomware attack is to invest in anti-malware/antivirus protection, preferably one that offers real-time protection designed to thwart advanced malware attacks such as ransomware. You should also look out for features that will both shield vulnerable programs from threats (an anti-exploit technology), as well as block ransomware from holding files hostage (an anti-ransomware component). Some anti-malware solutions offer rollback technology, especially designed to counter the effects of ransomware.
Next, as much as it may pain you, you need to create secure backups of your data on a regular basis. Our recommendation is to use cloud storage that includes high-level encryption and multi-factor authentication. Another option is to purchase USBs or an external hard drive where you can save new or updated files—just be sure to physically disconnect the devices from your computer after backing up, otherwise they could become infected with ransomware too.
Then, make sure your systems and software are updated regularly. The WannaCry ransomware outbreak took advantage of a vulnerability in Microsoft software, and while the company had released a patch for the security loophole back in March 2017, many folks didn’t install the update—which left them open to attack. We get that it’s hard to stay on top of an ever-growing list of updates from an ever-growing list of software and applications you use in your daily life. That’s why we recommend changing your settings to enable automatic updating.
Finally, stay informed. One of the most common ways that computers are infected with ransomware is through social engineering. Educate yourself (and your employees if you’re a business owner) on how to detect phishing emails, suspicious websites, and other scams. And above all else, exercise common sense. If it seems suspect, it probably is.
How can I remove Ryuk?
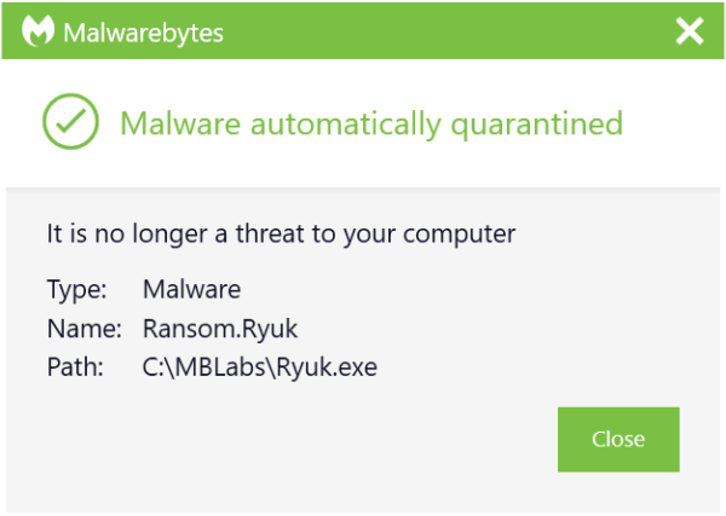
You can use the Malwarebytes Anti-Malware Nebula console to scan your endpoints. Choose the Scan + Quarantine option. Afterwards, you can check the Detections page to see which threats were found. On the Quarantine page you can see which threats were quarantined and restore them if necessary. Take a close look at the Detections page to see if you can find the answer to how Ryuk was delivered. You do not want to leave any backdoors behind that the attackers can use again!
If you suspect the delivery of Ryuk has been carried out by Emotet, you will need to perform some extra steps. If your computer is connected to a network—isolate it immediately. Once isolated, make sure you patch and clean the infected system. But that’s not all. Because of the way Emotet spreads across your network, a clean computer can be re-infected when plugged back into an infected network. Clean each computer on your network one-by-one. It’s a tedious process, but Malwarebytes business solutions can make it easier, isolating and remediating infected endpoints and offering proactive protection against future Emotet infections.