We’ve seen a fair few spam emails in circulation this week, ranging from phishing to money muling to sexploitation. Shall we take a look?
The FBI wants to give you back your money
First out of the gate, we have a missive claiming to be from the FBI. Turns out you lost a huge sum of money that you somehow don’t have any recollection of, and now the FBI wants to give it back to you via Western Union.
Sounds 100 percent legit, right? Here’s the email. See what you think:
Attn: BeneficiaryAfter proper and several investigations and research at Western Union and Money Gram Office, we found your name in Western Union database among those that have sent money through Western Union and this proves that you have truly been swindled by those unscrupulous persons by sending money to them through Western Union/Money Gram in the course of getting one fund or the other that is not real.
In this regard a meeting was held between the Board of Directors of WESTERN UNION, MONEYGRAM, the FBI alongside with the Ministry of Finance, As a consequence of our investigations it was agreed that the sum of One Million Five Hundred Thousand United States Dollars (U.S.1,500,000.00) should be transferred to you out from the funds that The United States Department of the Treasury has set aside as compensation payment for scam victims.
This case would be handled and supervised by the FBI. We have submitted your details to them so that your funds can be transferred to you. Contact the Western Union agent office through the information below:
Contact Person: Graham Collins Address: Western Union Post Office, California Email: westernunionofficemail0012@[redacted]
Yours sincerely, Christopher A. Wray FBI Director
Sadly, the FBI are not going to discover you’re owed millions of dollars then send you off to deal with a Western Union rep to reclaim it. Additionally, a quick search on multiple portions of the text will reveal parts of the above message dating back many years. It’s a common scam tactic to lazily grab whatever text is available then reword it a little bit for a fresh sheen. For example, here’s one from 2013 that came with a malicious executable attachment.
This one has no such nasties lurking, but someone could still be at risk of falling into a money mule scam, or losing a ton of cash from getting involved. The good news is that ancient text reuse tends to send up the spam filter flags for most email clients, so if you do come across this, there’s a good chance it’ll be stuffed inside your spam bin where it belongs. If it’s in there, hammer the delete button and forget about it.
Let’s go Apple phishing
Next up, a pair of Apple phishes:
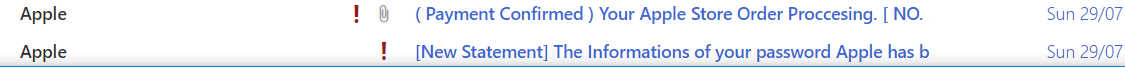
Click to enlarge
The first links to a site that’s currently offline, but does try to bait potential victims with a fake transaction for a set of $299 headphones:

Click to enlarge
As with most of these scams, they’re hoping you’ll see the amount supposedly paid, then run to the linked site and fill in the phishing form.
The text from the second one reads as follows:
Your Apple ID has been Locked This Apple ID [EMAIL ADDRESS] has been locked for security reasons.It looks like your account is outdated and requires updated account ownership information so we can protect your account and improve our services to maintain your privacy.
To continue using the Apple ID service, we advise you to update the information about your account ownership.
Update Account Apple ID For the security of your account, we advise not to notify your account password to anyone. If you have problems updating your account, please visit Apple Support.
A clickable link leads to the below phishing site located at appelid(dot)idnotice(dot)info-account-update-limiteds(dot)com:
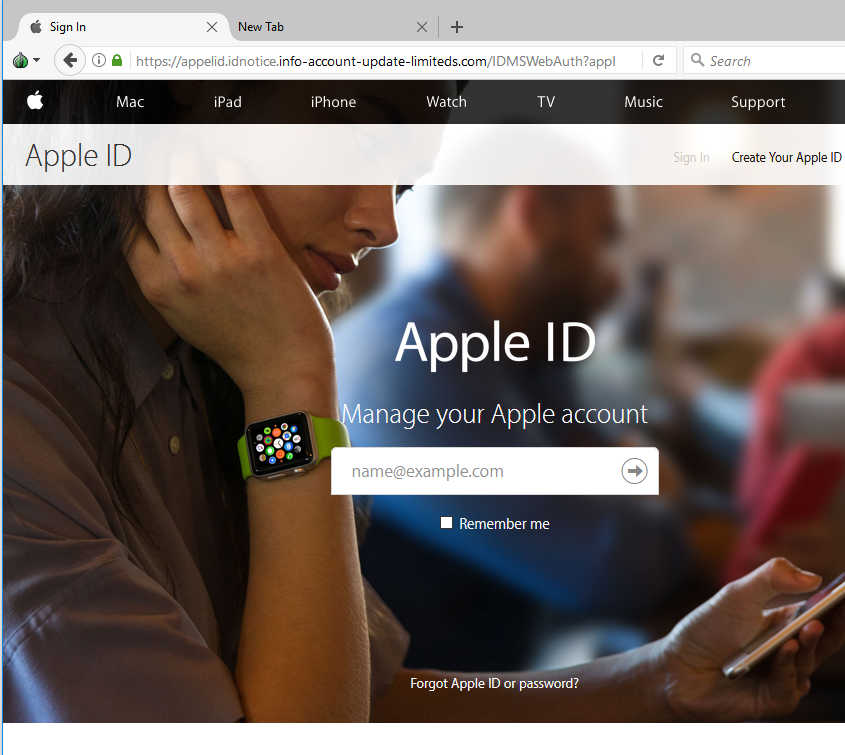
Click to enlarge
Upon entering a username and password, the site claims the account has been locked and needs to be set back to full health.
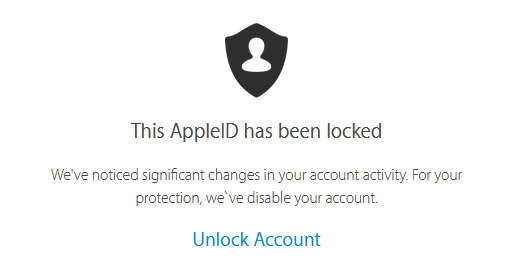
Click to enlarge
Potential victims are directed to a page asking for name, address, DOB, payment information, and a variety of selectable security questions.
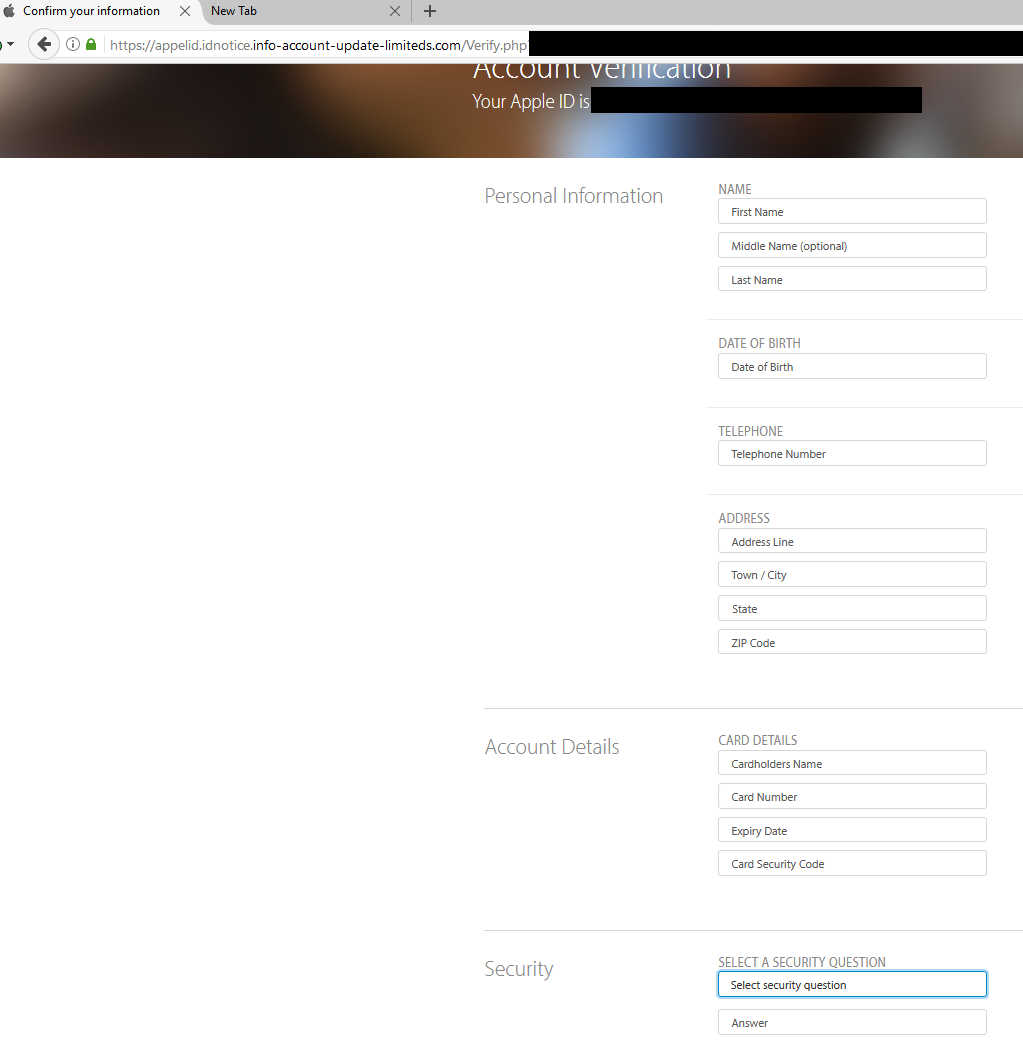
Click to enlarge
We don’t want anybody handing over personal information to scam mails such as the above, much less any fake login portals further down the chain. Always be cautious when seeing wild claims of payments and mysterious orders you have no recollection of; the name of the game is not so much panic buying as panic clicking, and that can lead to only one thing: hours spent dealing with the customer support section of shopping portals or your bank.
Sexploitation, Bitcoin, and old passwords
Speaking of mysterious behavior you have no recollection of participating in, a recent, massive phish email first hooks users by divulging their real, former password in the subject line, and then telling said recipients they’ve been caught on camera looking at porn and, um, doing other stuff.
Now, the drop of a password, even an old one, is enough to get many readers to raise a brow and open the email. Once opened, though, one of two things can happen. Those who haven’t viewed porn on their computer can breathe a sigh of relief. For the millions of others who have, however, a little panic might ensue, especially when the scammers ask for $7,000 in Bitcoin for hush money.
The email reads as follows:
I am well aware [redacted] is your password. Lets get directly to purpose. You don’t know me and you are probably thinking why you’re getting this email? Not a single person has compensated me to check you.
Let me tell you, I setup a malware on the xxx videos (porn material) web-site and you know what, you visited this website to experience fun (you know what I mean). When you were watching video clips, your web browser began functioning as a RDP that has a key logger which provided me with accessibility to your display as well as web cam. Right after that, my software collected all of your contacts from your Messenger, Facebook, as well as emailaccount. After that I made a double video. First part displays the video you were watching (you’ve got a good taste rofl), and next part displays the view of your webcam, & its you.
You actually have two different possibilities. Shall we review each one of these solutions in aspects:
Very first option is to just ignore this email. In such a case, I will send out your actual recorded material to every bit of your personal contacts and thus think about regarding the embarrassment you will see. In addition if you are in a romantic relationship, how it would affect?
2nd solution is to give me $7000. I will call it a donation. Then, I most certainly will straightaway discard your video footage. You will continue on with your way of life like this never occurred and you will not ever hear back again from me.
You’ll make the payment by Bitcoin (if you do not know this, search “how to buy bitcoin” in Google).
BTC Address: 14Fg5D24cxseFXQXv89PJCHmsTM74iGyDb
[CASE-SENSITIVE copy and paste it]
If you may be wondering about going to the authorities, good, this email can not be traced back to me. I have covered my actions. I am just not attempting to charge you very much, I only want to be compensated. I’ve a special pixel within this email, and now I know that you have read this e mail. You have one day to pay. If I do not get the BitCoins, I will definitely send out your video recording to all of your contacts including friends and family, colleagues, and many others. Nevertheless, if I do get paid, I’ll destroy the recording right away. It’s a non-negotiable offer, thus don’t waste mine time and yours by responding to this message. If you want to have evidence, reply with Yup! and I definitely will send your video to your 9 contacts.
This sextortion scam has been around for quite a while; the new twist is the use of real passwords. According to Krebs on Security, the scammers likely collected these passwords and emails from a data dump possibly dating back 10 years or more. Our own Malwarebytes researchers have been scouring various data dumps looking for the source of the breach, but so far have not found the smoking gun. The problem is that most users’ credentials have been swiped in one breach or another, if not multiple—if not dozens! So it’s difficult to triangulate and trace back to a single source.
The good news is, if you received one of these emails, you simply need only flag it as spam and delete. And if you’re suddenly worried about someone being able to see your nocturnal activities, you can buy a webcam cover for between $US5 and $10.










