Mobile Menace Monday is a bi-monthly entry to the Malwarebytes Labs wherein our Android OS security experts highlight the specific dangers of certain apps for today’s adaptable and heavily connected users. Expect mentions of bad apps, feedback to Android news, and some practical mobile security wisdom.
To nobody’s surprise, a new mobile Trojan has been found using the popular game Pokémon Go as bait. First spotted in mid-August, this Trojan uses the same package name and icon as the creature-catching game, making it more difficult for users to differentiate this fake from the real one.

The first thing the app does when installed is to ask for Device Admin rights.
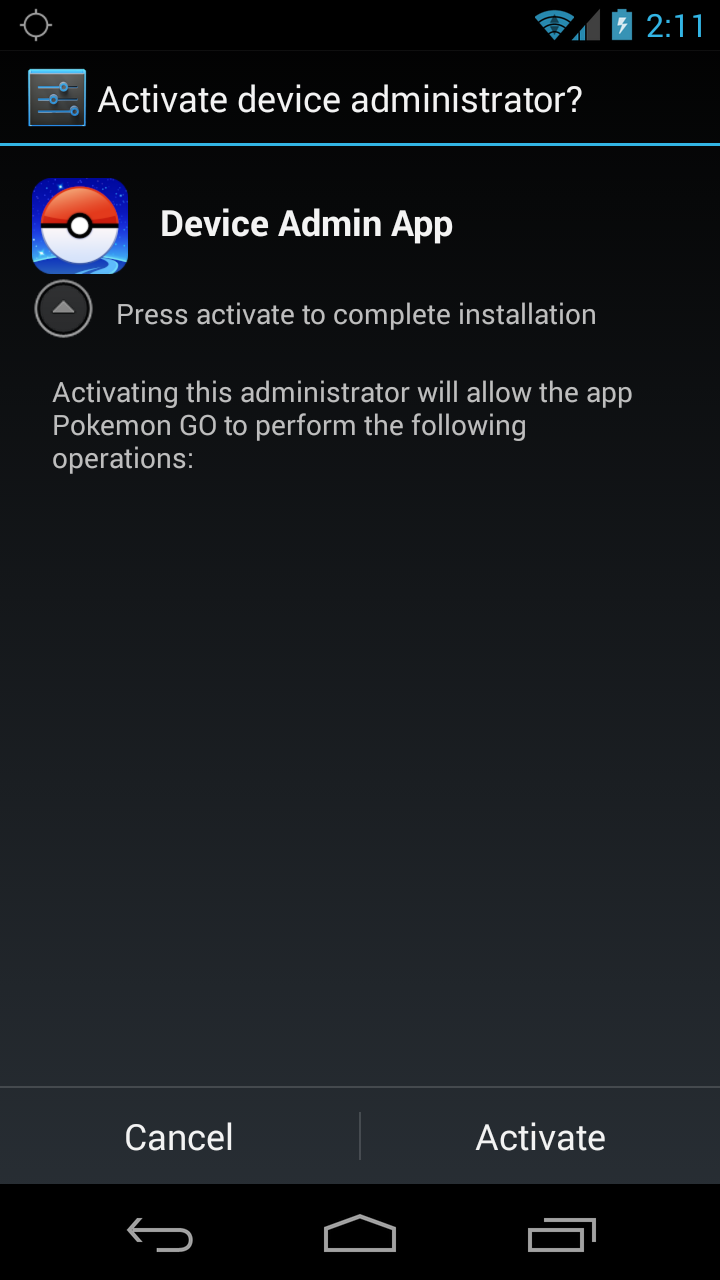
Activating this administrator will allow the app Pokemon GO to perform the following operations.
Other than making it more difficult for users and AV programs to uninstall the app (you have to go through the extra step of removing the app from the Device Admin list), it does not appear to use the heightened rights for any harmful operations.
If for some reason users do activate Device Admin rights—I’ll spare you the lecture of why you shouldn’t—and they install it, this app opens a browser to the hardcoded website, dior-aroma[DOT]ru/TYm3hm. The purpose of this site is to immediately redirect users to random destinations, such as this dating site below, in order to lure them into entering their personal information.
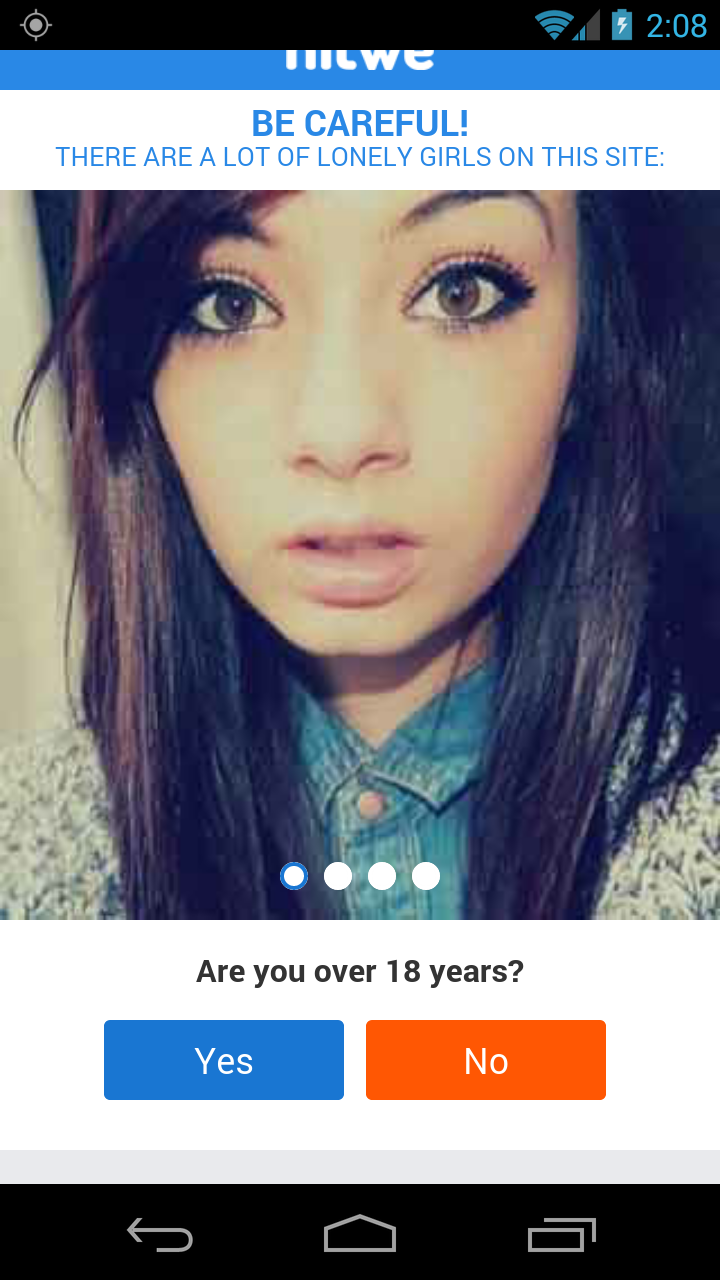
“>
Other destinations are sweepstakes that claim you won a prize that needs to be redeemed, surveys, or anything else that may convince users into entering information.
As you can see, it’s not the most hi-tech mobile malware. In fact, the authors are so lazy they used an automated app builder to create this fake Pokémon Go app. These automated app builders are so easy to use that just about anyone could create a simplistic app like this. Thus, it doesn’t deserve a better name than Android/Trojan.Agent.
Rest assured that this won’t be the last mobile malware exploiting Pokémon Go, but it may be the most thrown together.
Indicators of compromise (IOC):
- SHA256: 165a5d949a9cba33d1df741ca0d2fe6cdc5a1881bce29441c1fd2f4e0c8f15fb
- SHA256: 311fb28e1fc23d21caf78eba87815dd043a5833e96588b71fdb6cafb1e243bbc
- SHA256: 3fac298d60d76cb7de787531431f1e98d3a138cbadb976da7c78cfd3bc35868d










