Businesses adapting multi-factor authentication (MFA) continue to increase, and you can bet that cybercriminals are aware of this, too. This is why, according to the Microsoft Detection and Response Team (DART), more and more cybercriminals are angling their attacks towards stealing account authentication tokens instead of the usual username-password combo to completely bypass MFA and gain access to otherwise restricted resources.
“This poses to be a concerning tactic for defenders because the expertise needed to compromise a token is very low, is hard to detect, and few organizations have token theft mitigations in their incident response plan,” said DART in a blog post.
An authentication token (aka security token) is what identity platforms like Okta, Azure AD, Auth0, and OneLogin (to name a few) issue to a user once they have successfully proven they are who they say they are based on their username, password, and MFA per their company’s policy. A token not only gives users access to resources exclusive to their organization but also a level of practicality and convenience. At the backend, tokens authenticate every single request coming from pages, scripts, images, etc., so users don’t have to enter their credentials and MFA every time.
If a cybercriminal steals an authentication token, they wouldn’t need credentials to take over accounts and gain access to company resources. This is because a token contains a trusted user identity recognized by the domain a user interacts with. That said, authentication tokens must be protected against theft.
Gunning for tokens
Such a high value is now placed on authentication tokens that, according to Microsoft’s DART, the sneaky tactics to steal those tokens—such as Adversary-in-the-Middle (AitM)attacks—are increasing.
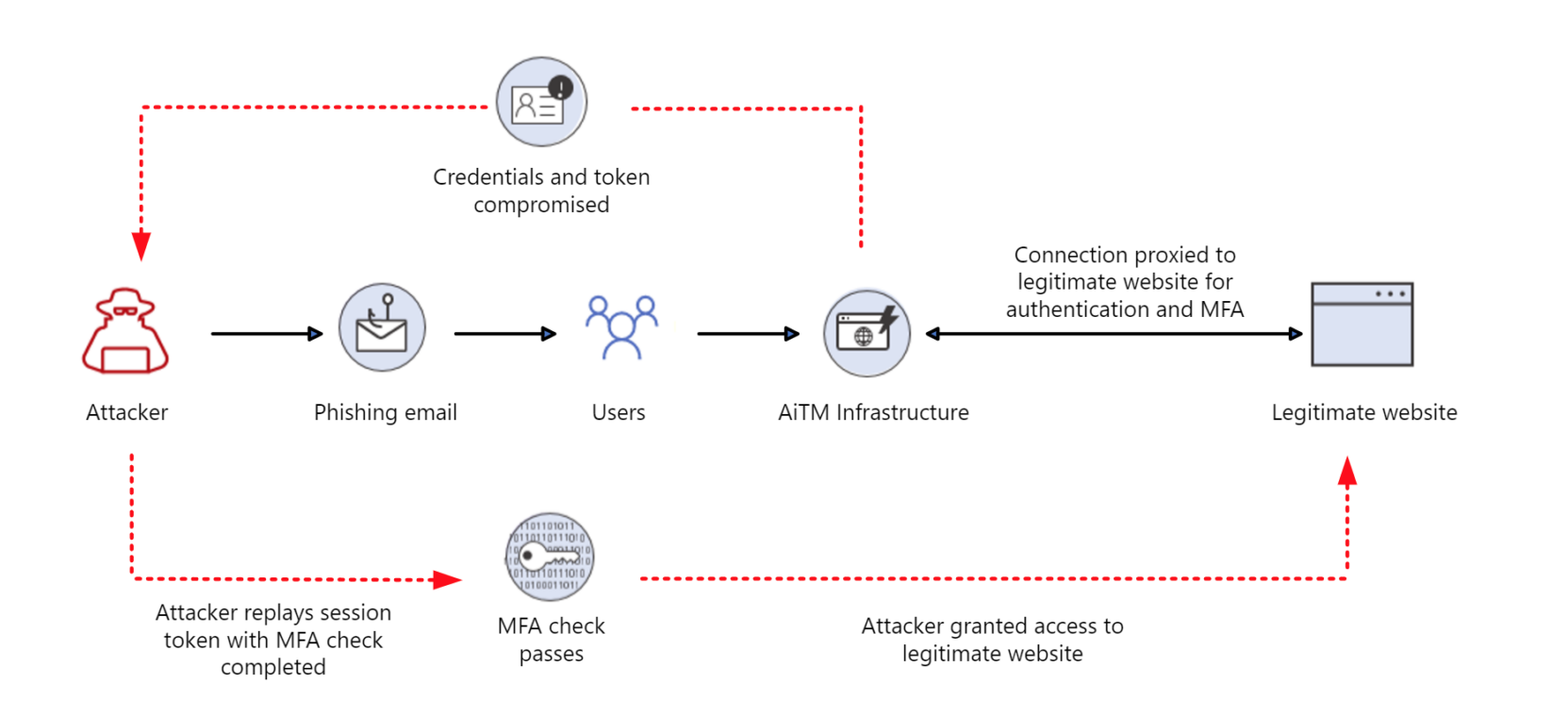
Microsoft explains: “Frameworks like Evilginx2 go far beyond credential phishing, by inserting malicious infrastructure between the user and the legitimate application the user is trying to access. When the user is phished, the malicious infrastructure captures both the credentials of the user, and the token.”
Another method to bypass MFA is the pass-the-cookie attack. It’s an attack wherein cybercriminals go after the cookies in your browser.
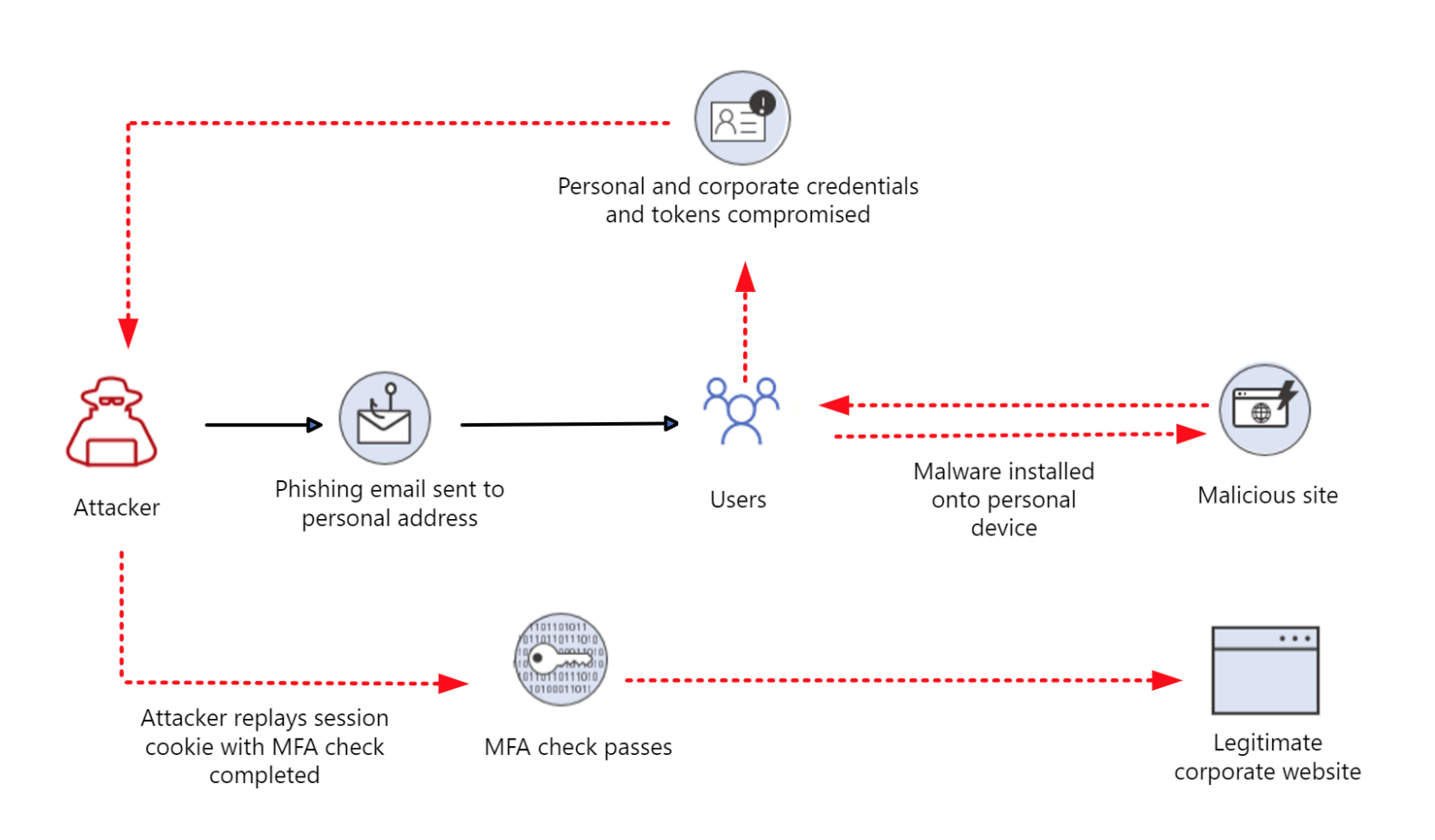
Although cookies and tokens are different, both store authentication data. For cookies, however, the data only lasts for a session. If cybercriminals can get their hands on a browser cookie, they can pass that to a different browser on another computer and use it to bypass security checkpoints.
Because many organizations continue to allow a hybrid setup, employees who work from home and also use their personal devices to log in and access corporate resources are particularly at risk of this attack. In contrast to corporate-managed devices, personal devices are considered less secure. And since it also lacks visibility from the IT team, it’s very difficult to determine if such devices have already been compromised.
This is why cybersecurity professionals advise employees to never use their personal devices for work use. Not only is corporate data at risk, personal accounts they access via the device are at risk as well.
Emotet, RedLine, and IcedID—all commodity credential theft malware—have built-in capabilities to steal cookies.
How to stop token thieves
A way organizations can make stealing authentication tokens difficult for cybercriminals is by encrypting the connection between the user and the system they’re interacting with using an encryption protocol, such as TLS (Transport Layer Protocol).
Microsoft further advises organizations to ensure that every device accessing company resources, remotely or not, is a known device visible to the IT team. Businesses must also plan and implement MFA solutions that are resistant to phishing attempts by using FIDO2 physical security keys, especially for company users with higher privilege than most.
Lastly, the company encourages businesses to keep practicing basic security hygiene, such as using endpoint protection, limiting access privileges, keeping all software updated or patched, along with using MFA solutions as a combination of all these protects against 98 percent of attacks.
While we’re seeing greater adoption of MFA, we’re also seeing cybercriminals going for the next weakest link to exploit: authentication tokens. Expect token theft to increase. But also, it’s high time organizations start considering the use of better security solutions, such as physical keys, for the greater security of everyone and every digital asset in the business.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.










