Results for 'facebook hack'
Malware in a Jar
April 3, 2013 - As researchers find more security flaws in Oracle Java, the software continues to be used for exploitation and malware delivery. This...
Dangerous beans: Oracle deep in the storm
March 6, 2013 - Last week security researchers from FireEye discovered a new Java exploit that works against the latest versions of Java (version 6...
Web Exploits: a bright future ahead
January 2, 2013 - The majority of computers get infected from visiting a specially crafted webpage that exploits one or multiple software vulnerabilities. It could...
Citadel: a cyber-criminal’s ultimate weapon?
November 5, 2012 - In old times, a citadel was a fortress used as the last line of defense. For cyber criminals it is a...
A Picture is worth a Thousand Messages
October 12, 2012 - Instant messaging is not a new concept; in fact, instant messaging software has been around for over 20 years in many...
Phishing 101: Part 3
July 13, 2012 - Over the last few weeks I have described numerous methods of phishing attacks and a few examples what they do or...
Phishing 101: Part 2
July 3, 2012 - “Over the years, phishing attacks have changed, as with most things, and have been segmented into different groups of variants.” –Me...
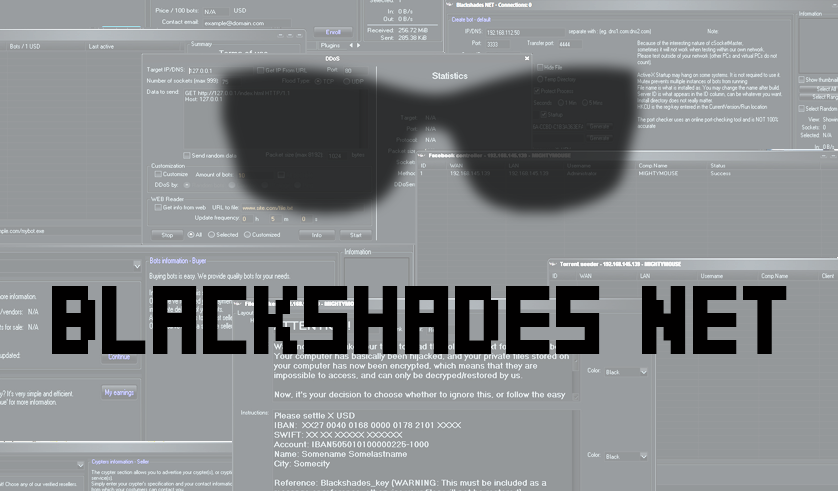
You Dirty RAT! Part 2 – BlackShades NET
June 15, 2012 - Last week we talked about the Remote Administration Trojan DarkComet and all the wonderful and scary things it can do. In...
You dirty RAT! Part 1: DarkComet
June 9, 2012 - Last week, I talked a little about the Flame Trojan and how much the average user would need to worry about...