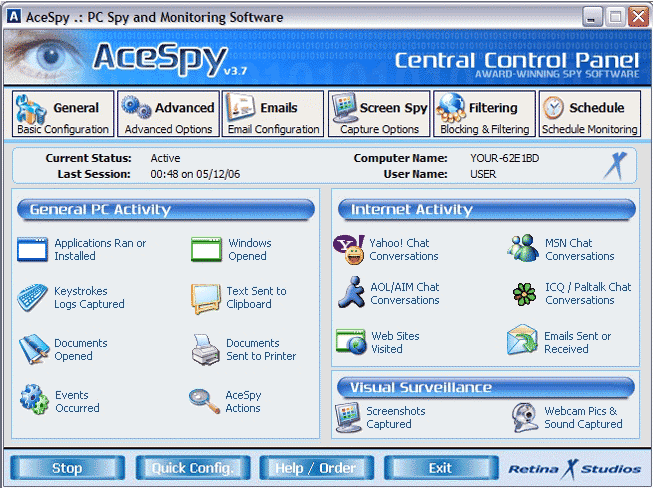
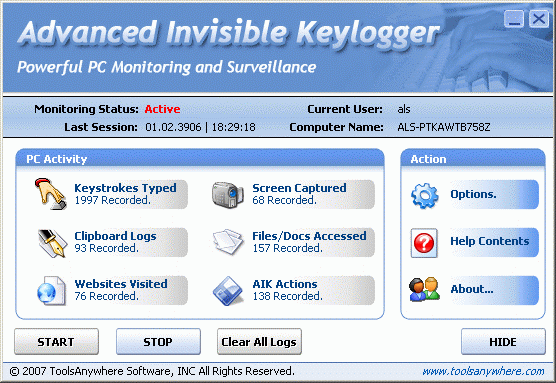
Short bio
Commercial keyloggers are applications designed to harvest user interactions with a computer. These interactions include the capture of keystrokes, usernames and passwords, screenshots, collection of images and sound from the microphone/camera, printed documents, browser history, emails, chat logs, and more. Commercial keyloggers are similar to Infostealers in their ability to covertly collect user information, but differ in the fact that these programs can be obtained with a legitimate license through legal means. Commercial keyloggers are often marketed toward concerned spouses/parents who wish to monitor usage of a home PC, corporate IT/security teams maintaining DLP protocols, and auditors checking for conformity to policy.
Commercial keyloggers are often polished applications featuring huge selections of monitoring and stealth capabilities to assist users in maintaining a long-term presence. Due to the low cost and vast availability of these types of applications, commercial keyloggers have long been a preferred choice for criminals seeking a low barrier of entry for identity theft and fraud activities.
History
The history of the use of keyloggers for surveillance purposes dates to the early days of computers. Wikipedia details various uses of keyloggers in the 1970s and early 1980s for various purposes including government clandestine operations. While various forms of keylogging have been occurring for quite some time, the boom in the creation and use of commercial keyloggers can be dated to the mid to late 1990s with a number of products quickly coming to market during that time. Since then, the number of commerical keyloggers available for purchase has exploded to thousands of different products with varying target audiences and in many languages.
Common infection method
Commercial keyloggers can be installed using a variety of methods or techniques. Considering the intended customer of such products, the majority of installations originate from a person who has physical access to the machine in question. Physical access to the machine will allow the person installing the software to properly configure any necessary settings to facilitate collection of desired information.
Other commercial keyloggers have fewer configuration settings, or the settings may be hardcoded via a custom builder. Installers configured in this manner require less interaction to ensure proper installation and thus can be installed via other means such as malspam, exploit, or social engineering.
Associated families
There are many commercial keylogger products and associated companies. Widestep, Refog, and SpyTech are all known producers of keylogger products. Well-known products include Elite Keylogger, Refog Free Keylogger, Realtime-Spy, Absolute Keylogger, PCSpy, Spy Lantern, and Ardamax Keylogger.
Remediation
Installing and running antivirus or anti-malware software on the affected system can automatically delete associated files and registry modifications. Many commercial keyloggers include an uninstall mechanism within the program configuration which can be used to remove all traces of the infection.
Aftermath
Commercial keyloggers by design attempt to collect all possible information about the users of the computer in which the software is installed. Therefore, it should be assumed that any and all personal information has been compromised if a commercial keylogger is found to be installed.
Avoidance
As in all cases, never click email or website links from unknown locations or install software at the urging of unknown parties. Using a reputable antivirus/anti-malware solution will help to ensure commerical keyloggers are unable to properly function, and will assist in mitigating any collection of data.