Short bio
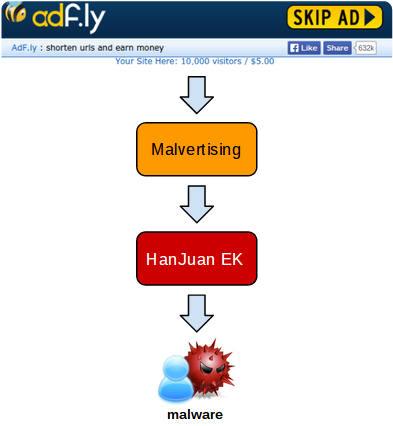
HanJuan is a stealthy exploit kit specialized in exploiting vulnerabilities in Internet Explorer, Silverlight, and Adobe Flash Player. Their attack vectors differ so much that it is sometimes hard to identify the exploit kit as HanJuan. They have been known to use redirects as well as serving malicious advertisements (malvertising). Due to advanced evasion techniques, which include IP blacklisting and using geolocation, the malware drops instigated by this exploit kit are often hard to reproduce and analyze.
History
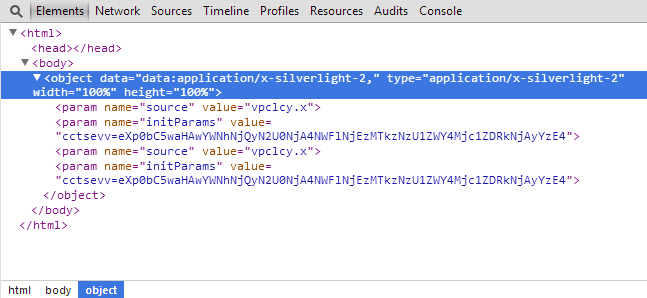
HanJuan is an advanced but relatively new player in the exploit kit market. First reports of it came about in early 2014 after it was first classified as unknown because it did not resemble any of the other exploit kits in method of infection. It was also among the first exploit kits to serve file-less infections. These infections run purely in the memory of the affected computer. No files are written to disk.
Common infection method
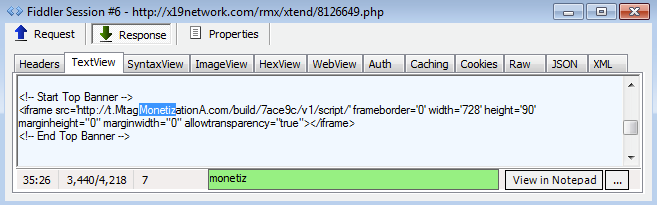
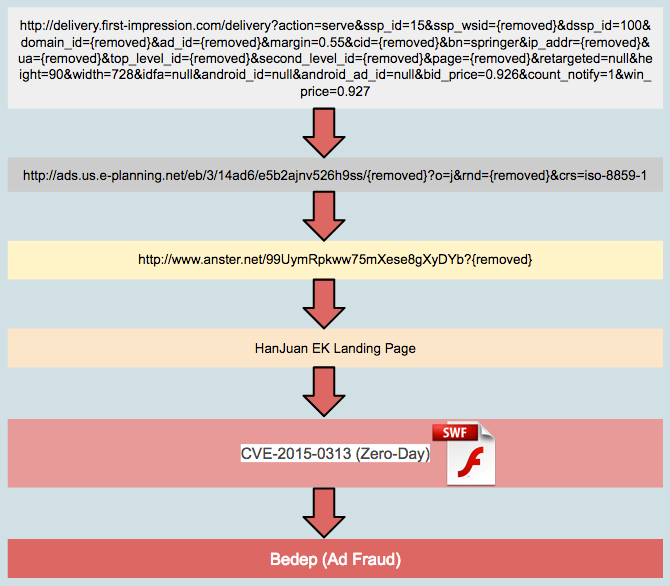
Typically exploit kits use known vulnerabilities to infect users. HanJuan uses both redirects from compromised sites and malvertising. The exploit kit then looks for vulnerable software (mainly Internet Explorer, Silverlight, and Flash) on the visitor’s computer and uses that as a way to infect the user. Only one vulnerability is tried at a time before they move on to the next if the previous attempt fails.
Associated families
The HanJuan exploit kit has some patterns in common with the Angler exploit kit, which leads us to believe they are related. In this case, HanJuan would be the one that is used for “special” customers.
HanJuan EK has been known to infect users with the Tinba Banking Trojan, Trojan.Agent.Kryptik, and Trojan.Agent.Fobber. In addition, CryptoLocker, Poweliks and Bedep have been reported to be pushed by this exploit kit.
Remediation
The redirection to the exploit kit’s landing page needs to be removed from the compromised site and the site itself needs to be patched and secured so it can’t be compromised again. In malvertising, the compromised ad network needs to remove the advertiser that pushes the redirects from their bidding system so they can no longer place bids to get their malvertising placed.
Aftermath
The options that you have to clean up the computer after being hit by an exploit kit depend greatly on the kind of malware that got dropped by the exploit kit. This can range from adware to password stealers. In some cases, it may be necessary to reformat the computer and change all your passwords.
Avoidance
Site owners should be vigilant about keeping their site secure and visitors should patch their browsers and their plugins. Doing so would only limit the risk, since they would still be vulnerable to zero-day exploits for which HanJuan is renowned. There are software solutions available that protect against zero-day exploits and will also stop known exploits. Advertising networks should not allow new advertisers to do any bidding before they have scrutinized their credentials and their ads.
Screenshots