v1hcmqbaqw.ru

Short bio
The domain v1hcmqbaqw.ru is blocked because it is associated with malwareof Russian origin, mostly bundlersand adware.
Protection
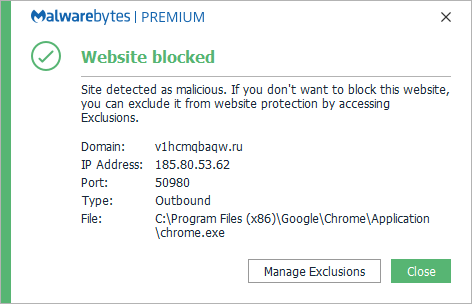
Malwarebytes blocks v1hcmqbaqw.ru
Add an exclusion
Should users wish to visit a blocked Domain and exclude it from being blocked, they can add it to the exclusions list. Here’s how to do it.
- Open Malwarebytes for Windows.
- Click the Detection History
- Click the Allow List
- To add an item to the Allow List, click Add.
- Select Allow a website.
- Select Add a URL and enter the domain that you wish to exclude.
- Click on Done and the domain should appear in your Allow List.




