Results for 'cloud'
Cloudflare Tunnel increasingly abused by cybercriminals
August 9, 2023 - Cloudflare Tunnel provides you with a secure way to connect your resources to Cloudflare without a publicly routable IP address. Cybercriminals...
Google fixes “Bad.Build” Cloud Build flaw, researchers say it’s not enough
July 20, 2023 - Researchers at Orca Security have found a design flaw in the Google Cloud Build service. Attackers would have been able to gain...
Western Digital confirms breach, affects My Cloud and SanDisk users
April 5, 2023 - Western Digital, a big brand in digital storage, says it has suffered a “network security incident—potentially ransomware—which resulted in a breach...
Multilingual skimmer fingerprints ‘secret shoppers’ via Cloudflare endpoint API
February 21, 2023 - One important aspect of data theft in criminal markets revolves around the authenticity of the data that is being resold. There...
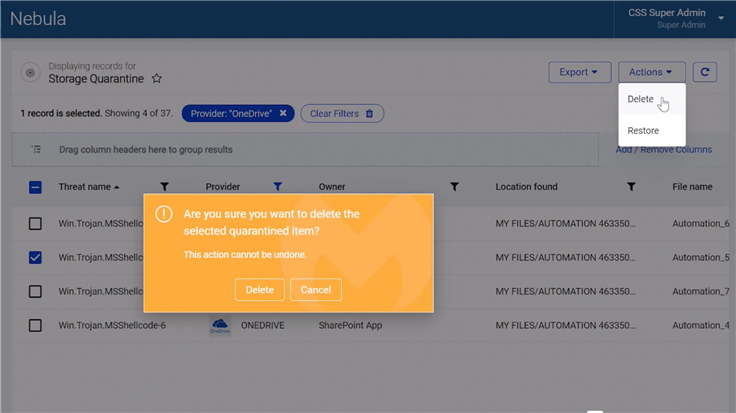
Introducing Quarantine for Cloud Storage Scanning in Nebula
December 14, 2022 - We’re excited to announce Quarantine for Malwarebytes Cloud Storage Scanning (CSS), a new feature which allows you to automatically quarantine threats...
Eufy “no cloud” security cameras streaming data to the cloud
December 5, 2022 - Eufy home security cameras are currently in a spot of trouble as a result of door camera footage. This is because...
Introducing Malwarebytes Cloud Storage Scanning: How to scan for malware in cloud file storage repositories
August 15, 2022 - We’re excited to announce Malwarebytes Cloud Storage Scanning, a new service that extends Nebula malware scanning options to include files stored...
Clouding the issue: what cloud threats lie in wait in 2022?
March 17, 2022 - As more services move ever cloud-wards, so too do thoughts by attackers as to how best exploit them. With all that...