Short bio
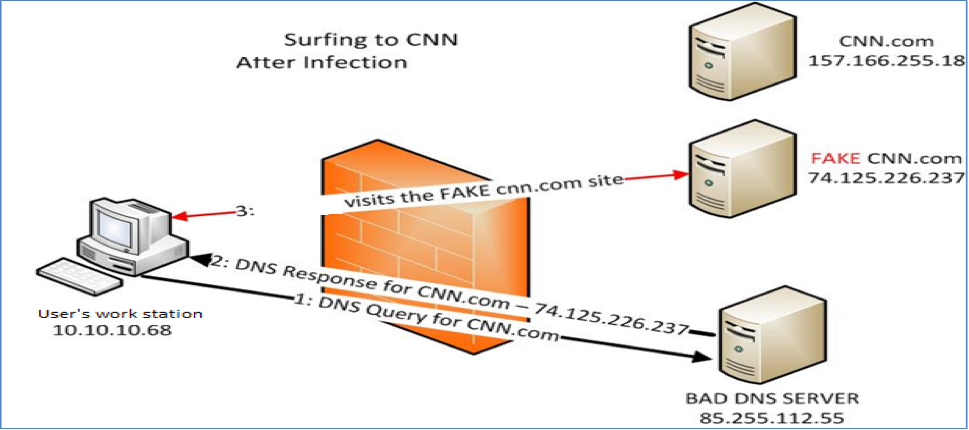
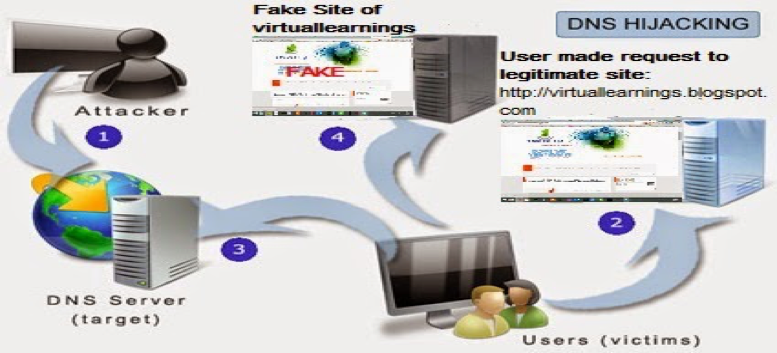
DNS changers/hijackers are Trojans crafted to modify infected systems’ DNS settings without the users’ knowledge or consent. Once the systems are infected and their DNS settings modified, systems use foreign DNS servers set up by the threat actors. Infected systems that attempt to access specific sites are redirected to sites specified by threat actors.
History
Domain Name System (DNS), is known as an Internet standard for the assigning of Internet Protocol (IP) addresses to domain names. Simply put, DNS interprets human-friendly host names to PC-friendly IP addresses.
It is common for users to automatically use DNS servers operated by their ISPs. Users who prefer more secure, faster, and more reliable DNS servers usually go with a third party service as ISP administered DNS servers can be slow and unreliable.
Cybercriminals have used DNS changers/hijackers for profit, as was seen with the Esthost/Rove Digital group.
Common Infection Method
DNS changers/hijackers are usually bundled with other malware such as rootkits, as seen in TDSS. Fake antivirus (FAKEAV) programs have also been used to spread DNS changer Trojans, as seen with Rove Digital.
Remediation
Use anti-malware software, such as Malwarebytes Anti-Malware to scan your infected system for DNS changer Trojans. If found, remove. You will want to contact your ISP and have them assist you with resetting your router settings. You will also need to reset your DNS settings, which is OS specific. DCWG is a great source of information on DNS changer remediation.
For example in Windows Vista/Windows 7 flush DNS:
- Click the start button and navigate to the command prompt (Start > All Programs > Accessories > Command Prompt)
- Make sure that you right click on the command prompt application and choose “Run as Administrator”
- Type in the command ipconfig /flushdns
Aftermath
Ensure your systems, OS, and applications are up-to-date with all current patches/updates. Recon your system for suspicious activity, check irregular/suspicious network traffic, and scan daily. If you are dealing with a rootkit such as TDDS, you will want to use rootkit removal tools.
Avoidance
Be vigilant and know what you are purchasing or downloading in terms of antivirus (AV) programs. Do your research about the AV company and the product.
Examples
Esthost/Rove Digital were a group of cybercriminals who planted DNS changer malware onto user systems and redirected their queries to malicious servers. Esthost/Rove Digital was able to redirect infected systems and implement difficult-to-detect attacks, which changed search results and replaced website advertising.
Before Apples OS X Snow Leopard was officially released, cybercriminals had already set up fake sites which claimed to provide the aforementioned Apple OS. In actuality, the sites actually dropped a DNS changer Trojan, which redirected users to other malicious sites.
Replacing of ad sites made lots of money for Rove Digital.
Victims who visited a known site like Amazon.com would see foreign ads instead of legitimate ads. Cybercriminals profited from ad impressions and clicks while the site owner did not see a profit.