This article is based on research by Marcelo Rivero, Malwarebytes’ ransomware specialist, who monitors information published by ransomware gangs on their Dark Web sites. In this report, “known attacks” are those where the victim did not pay a ransom. This provides the best overall picture of ransomware activity, but the true number of attacks is far higher.
July saw one of the highest number of ransomware attacks in 2023 at 441, second only to a record-breaking 556 attacks in May. At the forefront of these attacks is, once again, Cl0p.
In June, Cl0p shot to the top of the charts due to their use of a zero-day exploit in MOVEit Transfer, and victims from those attacks continued to be posted in July. The gang published the data of an additional 170 victims in July—the second highest number of attacks by a single gang all year, just two shy of MalasLockers’ record in May.
Amidst all the Cl0p chaos, however, a familiar foe seems to be quietly waning: LockBit.
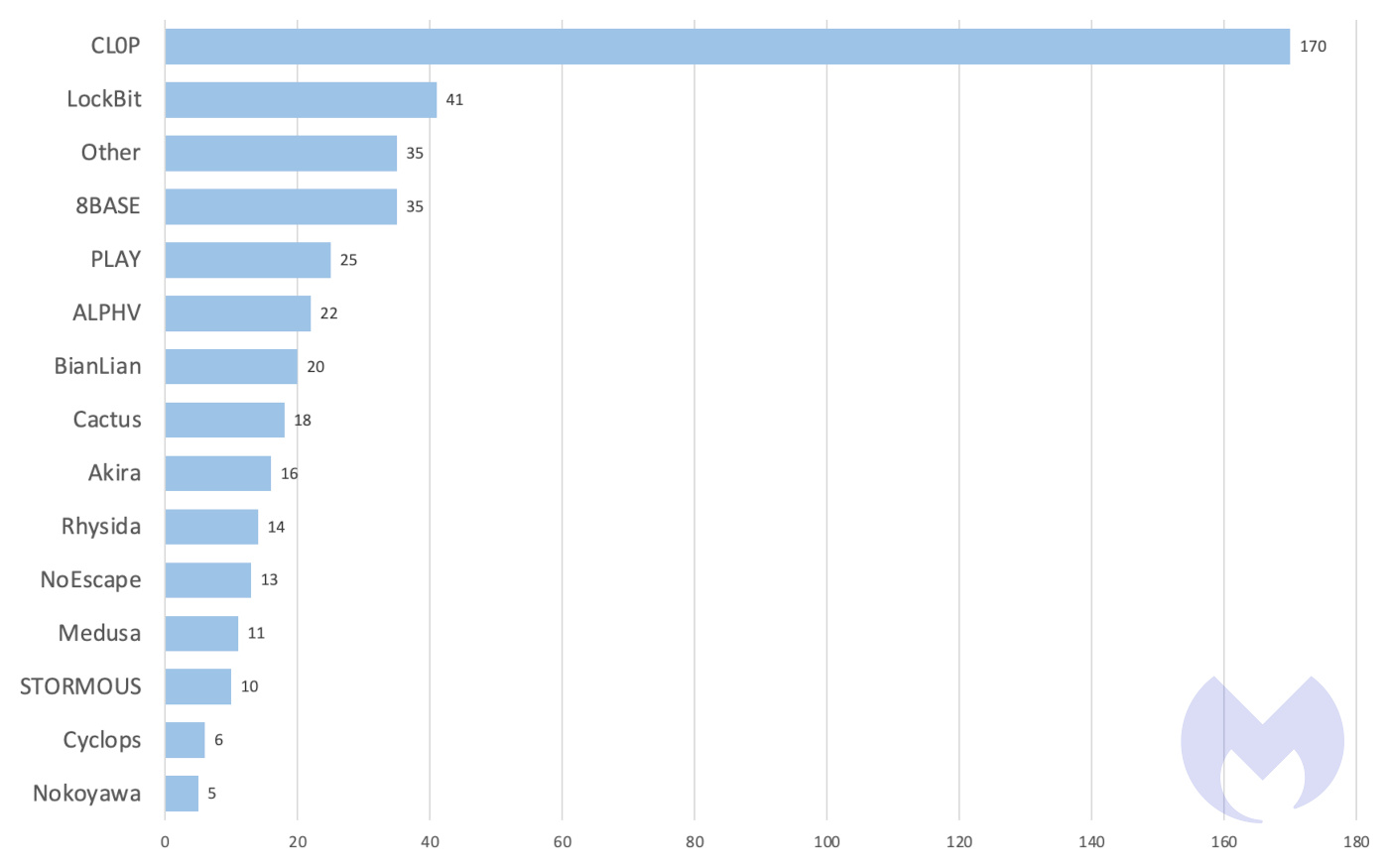
The LockBit gang is experiencing a steady four-month decline in the number of attacks it has carried out. Since April 2023, we’ve observed an average decrease of 20 attacks a month from the group. LockBit’s 107 attacks in April to 41 in July represents a 62 percent dip in activity.
We’ve seen a similar pattern from LockBit before, and it’s not unusual for ransomware gang activity to ebb and flow. Still, it’s worth mentioning that a suspected LockBit affiliate was arrested last month. At least LockBit’s July numbers, then, could be explained by them simply wanting to lay low for a bit.
When another LockBit suspected affiliate was arrested in November 2022, we also saw a similar historic low in activity from the group.
“Big game hunting” numbers
Research published in July by Chainanalysis showed that ransomware gangs raked in around $449 million from victims in the last six months. The driving force behind this huge number? Chainanalysis says it is “big game hunting.” the practice of targeting large, financially well-off corporations in order to secure the biggest possible payouts.
Chainanalysis also mentions an increase in payouts less than $1000, meaning smaller companies are still being targeted by ransomware gangs as well.
At around this same time last year, total payouts were slightly under $300 million—a difference of over $150 million.
One possible reason for this increase, says Chainanalysis, could be that because fewer and fewer firms are willing to pay the ransom, ransomware gangs are increasing the size of their ransom demands, the idea being to squeeze the most money possible out of the firms still willing to pay.
Malwarebytes’ own data suggests that the increase in payouts could also be a simple consequence of there being more ransomware attacks in general. From March 2022 to July 2022, Malwarebytes recorded a total of 1,140 ransomware attacks. From March 2023 to July 2023, we recorded a total of 2,130.
Likely, there’s a combination of factors at play here. Our logic goes as follows:
Bigger targets + greedier gangs + more ransomware attacks in general = Historically high payouts.
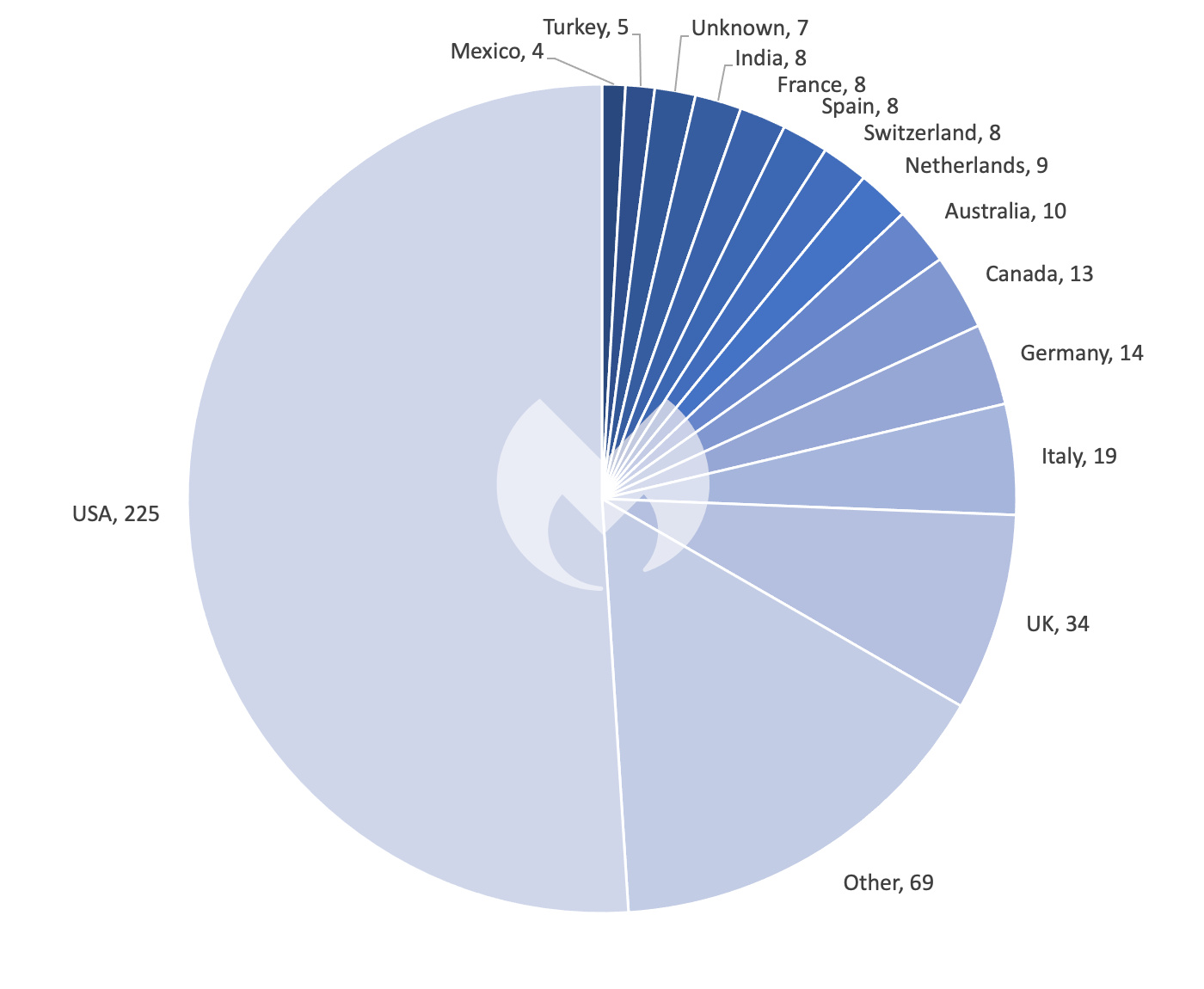
Attacks on the US and UK are at a four-month high. Four-mouth trends on attacks in Italy, on the other hand, suggest that the country is a new regular in the monthly “Top Five” of most-attacked countries.
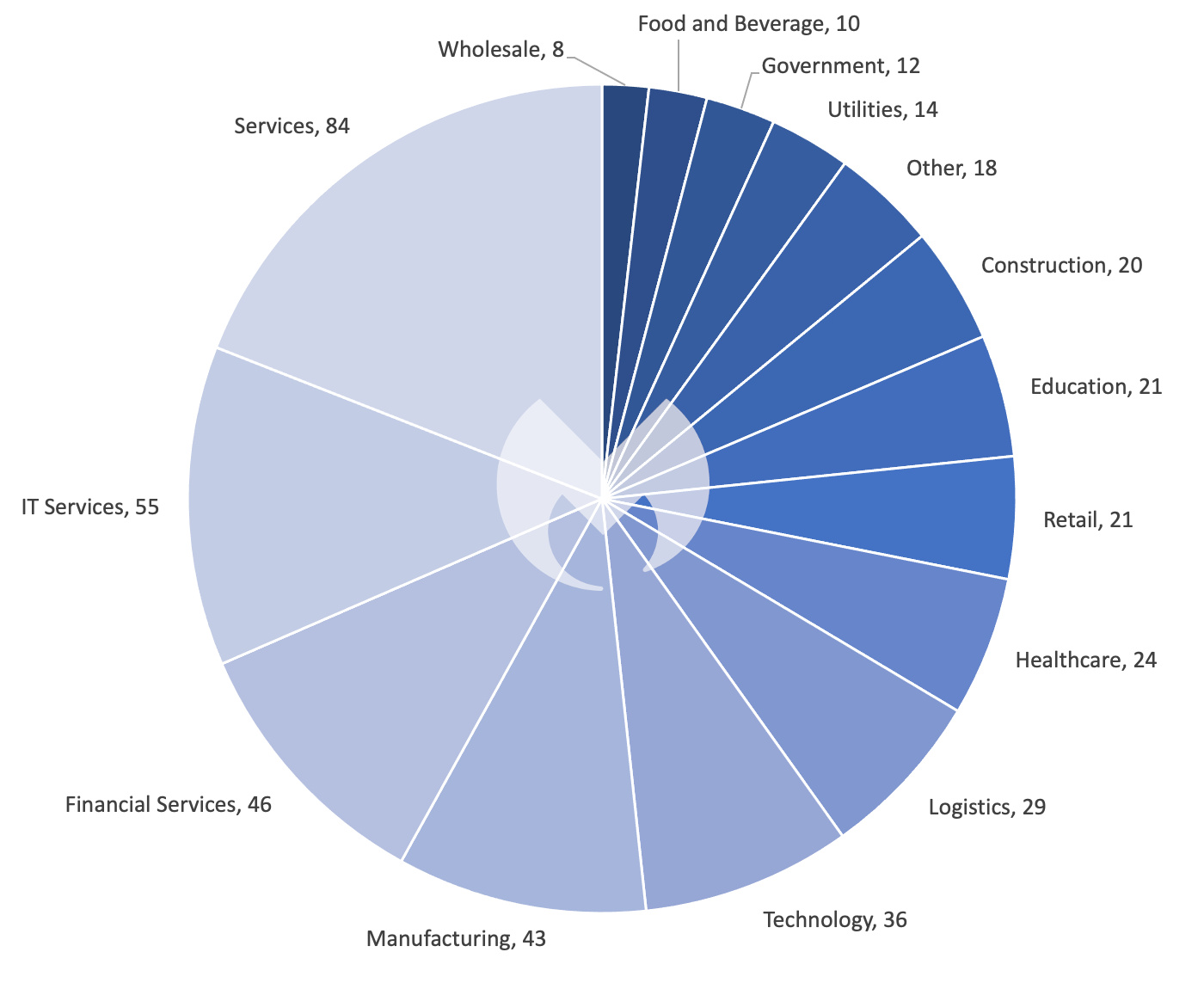
In an article published in October of last year, we speculated on the future evolution of ransomware and how, with the rise of double-extortion schemes, more and more gangs might pivot away from using encryptors entirely. Interestingly, new research last month by Huntress seems to support this idea—exemplified by the most active ransomware gang today no less.
In their massive zero-day exploitation sprees, Cl0p has apparently not deployed ransomware at all. Instead, the group has focused on simply stealing company data to then later use as leverage against victims.
This move represents a significant departure from the majority of top ransomware gangs, and it forces organizations to rethink the nature of the problem: i’s not about ransomware per se, it’s about an intruder in your network. The really dangerous thing is turning out to be the access, not the ransomware software itself.
Cl0p’s focus on exploiting zero-days for initial access is revolutionary on its own. Pairing this with a pure data-exfiltration approach could signal an even bigger paradigm shift in how ransomware gangs operate into the future.
Speaking of innovations from top gangs, last month ALPHV was observed offering an API for their data leak site.
The new API is a conduit for swift data dissemination, helping other cybercriminals instantly access and distribute the stolen information on the dark web. The overarching goal here —especially considering that ALPHV failed to seek a ransom from recently-breached cosmetics company Estee Lauder—seems to be to pressure victims to pay as stolen data reaches wider audiences.
Time will tell if the move pays off, but if nothing else, it signals cybercriminal desperation amid declining ransomware payments.
New players
CATCUS
CACTUS emerged in March 2023 as a fresh strain of ransomware, zeroing in on large-scale commercial operations. Last month, they published 18 victims on their leak site.
To infiltrate systems, this gang exploits well-known vulnerabilities present in VPNs. Once CACTUS operatives gain access to a network, they enumerate local and network user accounts and reachable endpoints. Following this, they craft new user accounts and deploy their ransomware encryptor. The uniqueness of CACTUS lies in their use of specialized scripts that automate the release and activation of the ransomware through scheduled tasks.

The CACTUS leak site
Cyclops/Knight
Though the underworld caught wind of Cyclops in May 2023, it’s only recently that evidence of their activities surfaced as new victims’ details appeared on their dark web portal. In addition, they’ve announced a shift in branding to “Knight.” Last month, they published 6 victims on their leak site.
This ransomware is versatile, capable of compromising Windows, Linux, and macOS systems alike. Cyclops stands out with its intricate encryption methodology, which mandates a unique key to decrypt the execution binary. Cyclops also comes equipped with a distinct stealer component designed to extract and transfer sensitive information.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; disable or harden remote access like RDP and VPNs; use endpoint security software that can detect exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like Malwarebytes EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Malwarebytes EDR and MDR removes all remnants of ransomware and prevents you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.










